In today’s world, securing data from various malicious threats is no longer a priority for just the medical, government or financial industries. It is a priority for every enterprise that wants to stay relevant. All enterprises, public or private are equally vulnerable to hackers, who are able to steal intellectual property or large quantities of customer information. FTC is aggressively taking action against companies that show negligence in protecting customers’ data. Ransomware attacks have become a daily occurrence; and every day we hear about companies or public organizations (e.g. the unfortunate breach at OPM!) losing incredibly sensitive customer data to hack attacks. In this day and age with this heightened awareness and with all the resources available, these breaches are inexcusable. In this and a series of subsequent blogs, we will discuss how Cohesity’s storage platform helps address these issues.
Cohesity’s vision is to be an end-all, be-all secondary storage platform. By our definition, secondary storage platform holds roughly 80% of enterprise data and presents a huge target to hackers, as was made apparent by the devastating Sony hack. Right from the very beginning we knew that we could not treat security as an afterthought and that we had to ‘bake’ it right into our platform! While security is reflected in everything we do, for now I will focus on four specific ways by which we distinguish ourselves from any other storage vendor in securing customer’s data:
- FIPS certified encryption architecture that is more secure than hardware-only encryption;
- Consolidation of secondary storage workflows into a single hyperconverged platform, that reduces complexity, eliminates redundancy and is data-aware;
- Virtual and physical data isolation to minimize breaches and provide multi-tenancy
- Unlimited and frequent backups that all but eliminate RTOs and RPOs.
Let’s talk about each one of them in more detail …
Encryption
Our file system provides full at-rest encryption based on the strong AES-256 standard. The encryption architecture provides this high security while maintaining the flexibility to optimally leverage the available hardware and software resources. Additionally, our encryption can be set to run under FIPS-certified mode.
We have built full software-based encryption that is hardware-accelerated through the latest Intel processors. With hardware acceleration, the software-based encryption route has become much faster (in the order of several GB/s), and thus has minimal impact on performance. While we also employ self-encrypting drives (SED), I believe that full software encryption provides us with greater flexibility.
Before I expand further, let me take a little segway and explain the difference between ‘FIPS-compliant’ and ‘FIPS-certified’. FIPS-compliant has no real meaning. If a vendor is using an encryption standard listed under FIPS requirements to encrypt some of the data, they can say their product is FIPS-compliant. To claim FIPS-certification, a vendor has to go through extensive sets of tests conducted by a federal government approved 3rd party lab. The certification is specific to that particular hardware-software combination and goes beyond the particular encryption algorithms used.
When we decided to get FIPS certification, we had to ensure that we could upgrade SSDs and HDDs without affecting the certification status. So we did two things: i) used encryption algorithms in our crypto module that are FIPS 140-2 level 2 certified ii) designed an option for software-only encryption that removed hardware component dependency. This allows us to maintain our FIPS certification while giving the flexibility to upgrade to denser/faster drives as they become available. If the customer doesn’t need FIPS certification then our platform intelligently uses software and hardware (SEDs) encryption to provide the best possible performance while maintaining same level of security.
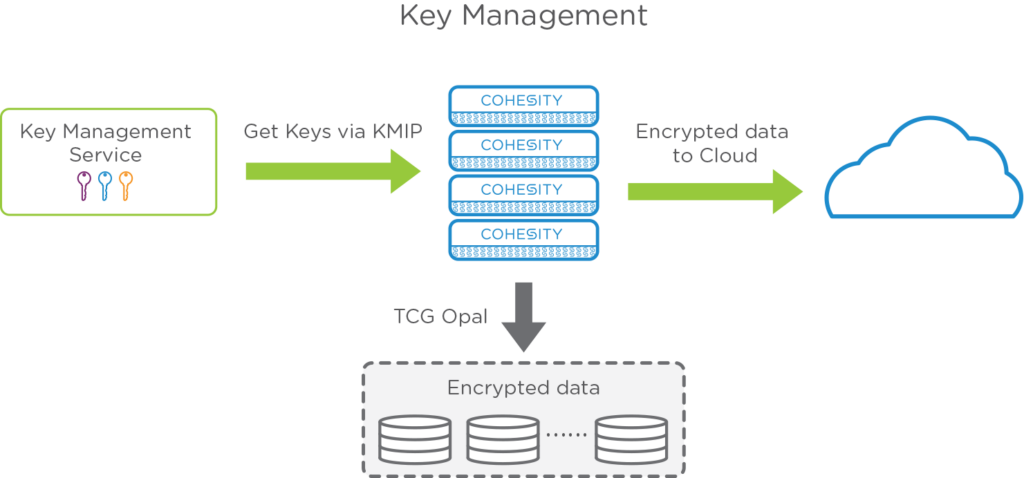
We also make sure that the encryption keys are automatically rotated with a cadence set by the users. Users don’t have to deal with managing the keys or any passwords. The solution provides the flexibility to use an external key manager, if available, or the Cohesity cluster can manage this on its own. An important thing to remember is that the data is not re-encrypted every time the key is changed.
Setting up encryption on your cluster takes just selecting a checkbox!
Security is more than just encryption. I strongly believe that security of the system is only as strong as the platform it is built upon. This is where Cohesity totally differentiates itself from any other system out there. My next three points talk about platform-related features that directly enhance the security.
Consolidation
Traditional storage architectures leverage many software and hardware components from many different vendors. This leads to complex license management and inefficiencies in workflow orchestration. More importantly, these legacy architectures lead to multiple copies of same data floating around in multiple systems with management having little insight into all its ‘data silos’. Making sure that your storage infrastructure is secure across all these components can be very challenging, if not impossible and error prone. Cohesity provides a hyperconverged storage solution, that has a robust framework to securely store your data at rest and consolidate all the secondary storage workflows into a single scale-out platform. It completely eliminates redundant copies and makes data available for fast analytics so that you are never in dark about the kind of data you are storing. This consolidation into a single platform architecture where data is governed by a central security policy is what I mean when I say that security is baked into the platform.
Data Isolation
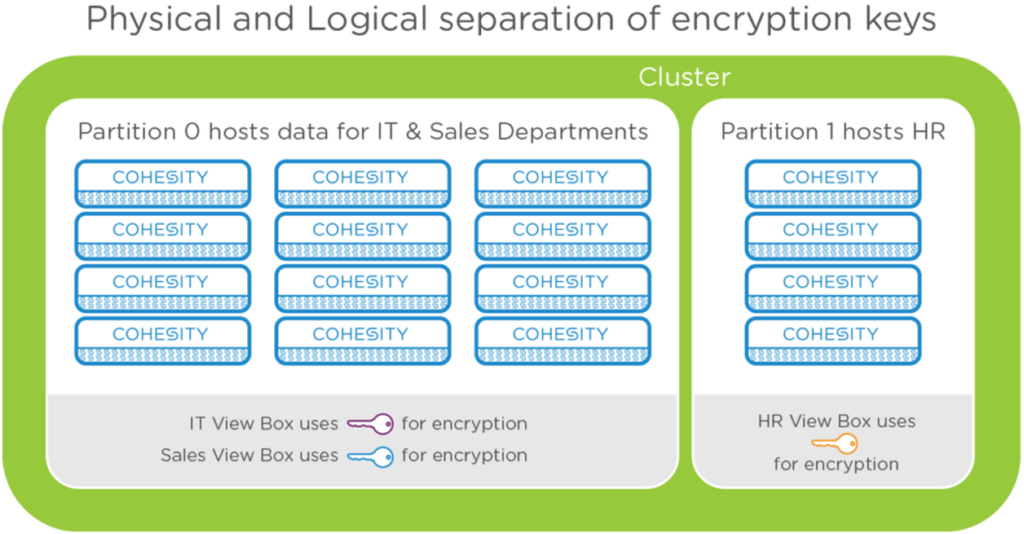
The platform is architected to provide physical and virtual data isolation through Partitions and View Boxes respectively. Partitions are complete physical isolations of compute and storage resources in a cluster so that should you choose, you can force given workloads to run only on particular hardware within the cluster. A View Box is a logical division of a partition, that contains one or more filesystems. Each of these View Boxes encrypt data ‘stored’ by them using their own independent keys. This allows for robust data isolation. For example, if IT data and financial data are on different view boxes, a breach on the IT data will not automatically risk your financial data.
Now, speaking about the data flow, the data usually arrives to the Cohesity cluster through secure channels or from a secure private network. From there on, it is encrypted based on the View Box it belongs to, and stored securely on SSDs, HDDs or a cloud tier.
I want to expand on the cloud part a bit. If you are already aware, Cohesity platform is fully integrated with the cloud. You can tier to the cloud, archive to the cloud and even run Cohesity in the cloud. We didn’t have to do anything extra to provide the same security to your cloud data as to your on-prem data. The full at-rest and in-flight encryption ensures that data is protected end-to-end.
Frequent Backups
One of the neatest features of Cohesity platform, the one that I believe, provides the most solid defense against Ransomware is its ability to all but eliminate RTOs and RPOs. Now bringing RTOs and RPOs into a security blog may seem strange but let me explain why it makes perfect sense here. The Ransomware attacks work by temporarily removing access to the working data set. If the company doesn’t pay up, the perpetrator removes access permanently. Bigger the impact of this data loss to business operation, higher the chance of businesses paying up the ‘ransom’. Now imagine a world where customer can do backups every minute and can restore to any point back in time almost instantly. If they can do that, then the worst they lose is a minute worth of data, so right there they have all but addressed the key downside of ransomware attacks. Additionally, an ability to go back to any ‘clean state’ almost instantly can let their security forensics to find out exactly when a particular security breach happened and how. Cohesity’s unique SnapTree™ technology allows them to do exactly that! It allows the customer to take any number of snapshots as often as they want while keeping each of the snapshots fully hydrated.
Security is more than just Encryption
I have barely scratched the surface on security here. Each one of the points discussed here deserve their own blog post. But if there is one message I want you to take from here is that security simply can’t be an afterthought. It has to be thought of before the first line of code is written, before the high level design is done and even before the business case for the product is made. I am extremely fortunate to be working with an experienced core team who is building such a complex system, the fourth time over! That’s why the security was built into the fabric of our distributed scale-out platform. Consolidation of workflows, FIPS-certified at-rest encryption, data isolation and SnapTree technology provide the multi-layer security that all work together to stop data breaches in your secondary storage and minimize the adverse consequences of breaches in your primary systems.