Incident command
SOC analysts detect a surge in unusual VPN logins from foreign IPs, followed by rapid file changes across shared drives.
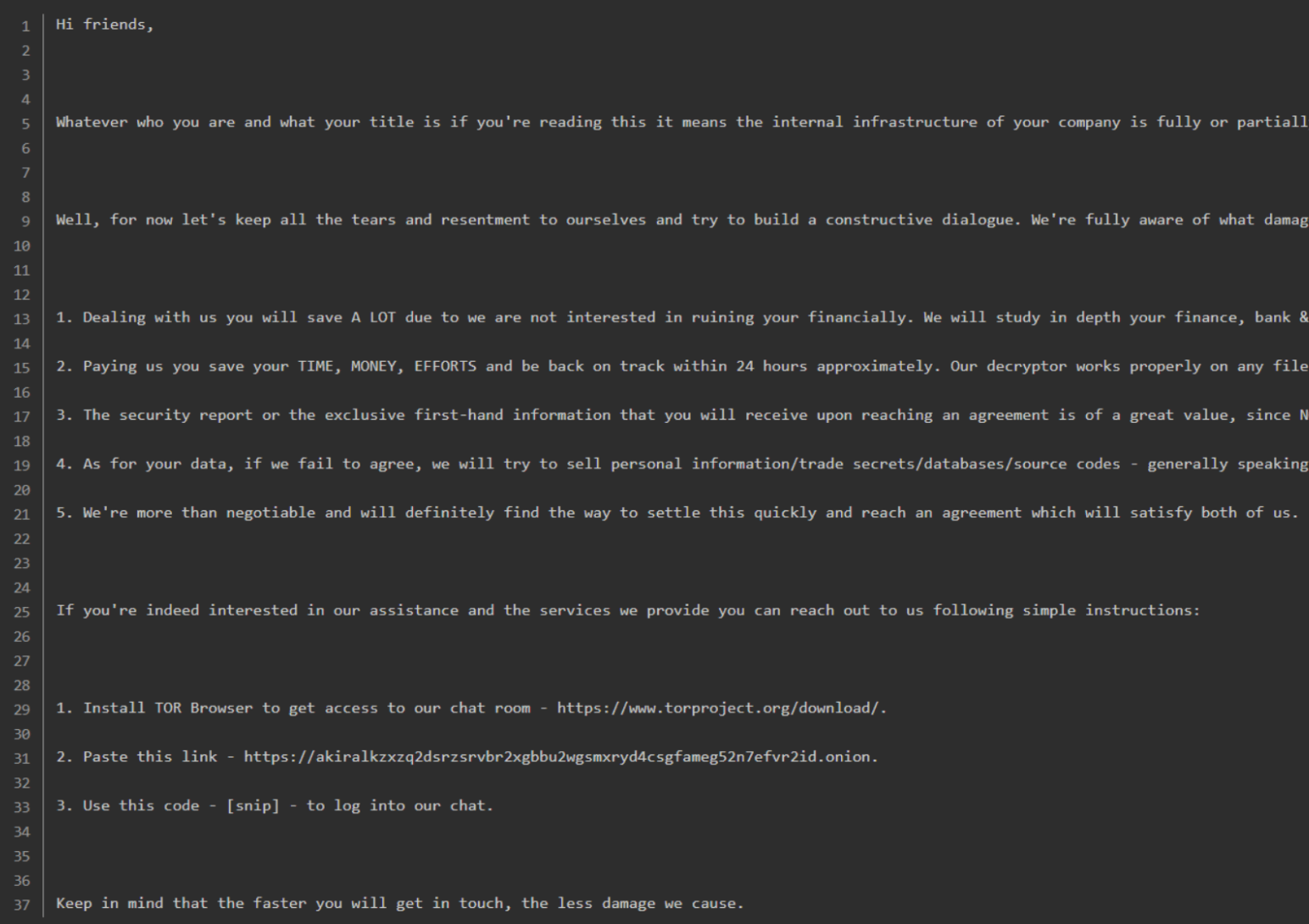
Soon after, the help desk receives a ticket reporting a suspicious file named “akira_readme.txt”—a likely ransomware note.

 Correct Answer
Correct Answer
Validate suspicious change rates in backup data. Search all Cohesity clusters for ransom notes. Send IOCs to your SIEM for broader threat detection.
 Incorrect answer
Incorrect answer
Rebooting affected servers to “clear” the issue can destroy important evidence and delay detection of active malware.
 Neutral Answer
Neutral Answer
Communication is important, but validating the threat early and scoping will help you stay ahead of the attacker.
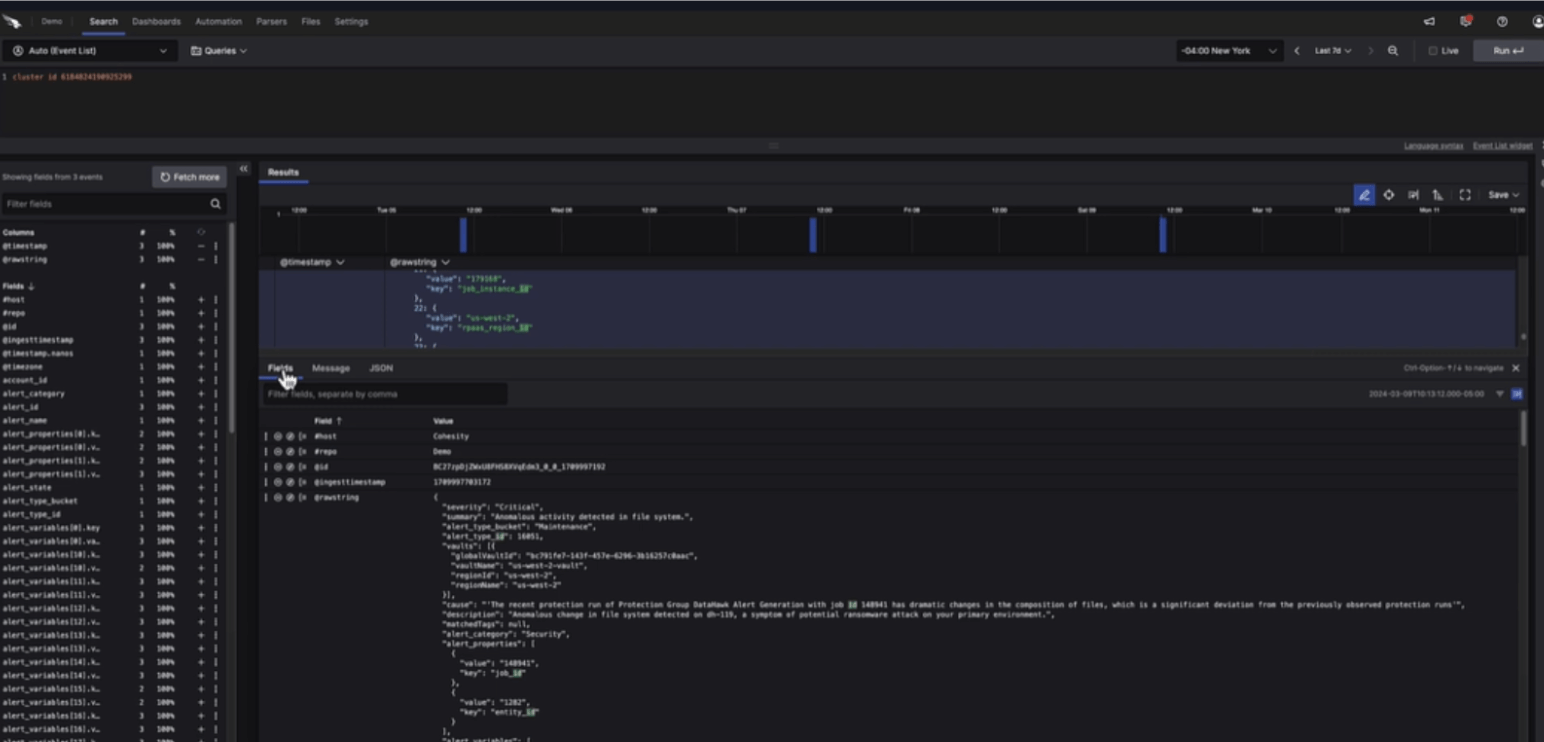
AI-based anomaly detection alerts from Cohesity Data Cloud show the alert isn’t a false positive.

Initiate the crisis management protocol, brief the board, prepare a press release, and begin organizing response resources.
SOC analysts detect a surge in unusual VPN logins from foreign IPs, followed by rapid file changes across shared drives.
Soon after, the help desk receives a ticket reporting a suspicious file named “akira_readme.txt”—a likely ransomware note.
Your move: How will you confirm the incident?
Review Cohesity anomaly alerts
Validate suspicious change rates in backup data. Search all Cohesity clusters for ransom notes. Send IOCs to your SIEM for broader threat detection.
SOC analysts detect a surge in unusual VPN logins from foreign IPs, followed by rapid file changes across shared drives.
Soon after, the help desk receives a ticket reporting a suspicious file named “akira_readme.txt”—a likely ransomware note.
Your move: How will you confirm the incident?
Review Cohesity anomaly alerts
Validate suspicious change rates in backup data. Search all Cohesity clusters for ransom notes. Send IOCs to your SIEM for broader threat detection.
SOC analysts detect a surge in unusual VPN logins from foreign IPs, followed by rapid file changes across shared drives.
Soon after, the help desk receives a ticket reporting a suspicious file named “akira_readme.txt”—a likely ransomware note.
Your move: How will you confirm the incident?
Review Cohesity anomaly alerts
Validate suspicious change rates in backup data. Search all Cohesity clusters for ransom notes. Send IOCs to your SIEM for broader threat detection.
Contain
With the incident declared, your priority now shifts to stopping the attacker’s movement and preserving forensic evidence.
Investigation shows the adversary entered via VPN without MFA. Endpoint telemetry flags AnyDesk beaconing to an external host, indicating remote control, and a new domain admin account “itadm”.
You’ve contained the threat, but response efforts may be slowed.

 Incorrect answer
Incorrect answer
That action destroyed valuable forensic evidence and may alert the attacker before containment is complete.
 Correct Answer
Correct Answer
Quickly establish a clean room to understand the attack and plan the appropriate remediations to prevent future attacks.
 Neutral Answer
Neutral Answer
Changing the password slows the attacker, but it doesn’t address other persistence mechanisms or preserve important evidence.

Engage Cohesity CERT to freeze your backup environment and support collection of logs and data. In partnership with leading IR teams, CERT accelerates coordination, information sharing, and secure recovery.

The Cohesity Clean Room solution provides a flexible, secure space to restore critical security tools and infrastructure essential for investigation and remediation.
With the incident declared, your priority now shifts to stopping the attacker’s movement and preserving forensic evidence.
Investigation shows the adversary entered via VPN without MFA. Endpoint telemetry flags AnyDesk beaconing to an external host, indicating remote control, and a new domain admin account “itadm”.
You’ve contained the threat, but response efforts may be slowed.
How will you start investigation and mitigation?
Establish an isolated environment
Quickly establish a clean room to understand the attack and plan the appropriate remediations to prevent future attacks.
With the incident declared, your priority now shifts to stopping the attacker’s movement and preserving forensic evidence.
Investigation shows the adversary entered via VPN without MFA. Endpoint telemetry flags AnyDesk beaconing to an external host, indicating remote control, and a new domain admin account “itadm”.
You’ve contained the threat, but response efforts may be slowed.
How will you start investigation and mitigation?
Establish an isolated environment
Quickly establish a clean room to understand the attack and plan the appropriate remediations to prevent future attacks.
With the incident declared, your priority now shifts to stopping the attacker’s movement and preserving forensic evidence.
Investigation shows the adversary entered via VPN without MFA. Endpoint telemetry flags AnyDesk beaconing to an external host, indicating remote control, and a new domain admin account “itadm”.
You’ve contained the threat, but response efforts may be slowed.
How will you start investigation and mitigation?
Establish an isolated environmen
Quickly establish a clean room to understand the attack and plan the appropriate remediations to prevent future attacks.
Eradicate
The investigation deepens. Analysis reveals stolen credentials from Windows memory and AD service accounts—a sign of advanced credential harvesting. The attacker also disabled antivirus tools to stay hidden and used Rclone and WinSCP to exfiltrate data.
The attacker’s footprint runs deep, and it’s time to root them out completely.

 Correct Answer
Correct Answer
Rotate credentials and tokens, hunt and remove unauthorized remote access, repeatedly scan mounted snapshots until clean, and select known-good point.
 Incorrect answer
Incorrect answer
Resuming production before confirming a clean state can reintroduce the attacker or reinfect critical systems.
 Neutral Answer
Neutral Answer
AV reinstalls may detect known threats but often miss hidden persistence or credential abuse.

Detect hidden malware faster by scanning Cohesity snapshots using curated threat intelligence, hash-based detection, and an extensive library of YARA rules.
The investigation deepens. Analysis reveals stolen credentials from Windows memory and AD service accounts—a sign of advanced credential harvesting. The attacker also disabled antivirus tools to stay hidden and used Rclone and WinSCP to exfiltrate data.
The attacker’s footprint runs deep, and it’s time to root them out completely.
How will you remove attacker persistence and validate a clean recovery point?
Rotate credentials/tokens and hunt for persistence
Rotate credentials and tokens, hunt and remove unauthorized remote access, repeatedly scan mounted snapshots until clean, and select known-good point.
The investigation deepens. Analysis reveals stolen credentials from Windows memory and AD service accounts—a sign of advanced credential harvesting. The attacker also disabled antivirus tools to stay hidden and used Rclone and WinSCP to exfiltrate data.
The attacker’s footprint runs deep, and it’s time to root them out completely.
How will you remove attacker persistence and validate a clean recovery point?
Rotate credentials/tokens and hunt for persistence
Rotate credentials and tokens, hunt and remove unauthorized remote access, repeatedly scan mounted snapshots until clean, and select known-good point.
The investigation deepens. Analysis reveals stolen credentials from Windows memory and AD service accounts—a sign of advanced credential harvesting. The attacker also disabled antivirus tools to stay hidden and used Rclone and WinSCP to exfiltrate data.
The attacker’s footprint runs deep, and it’s time to root them out completely.
How will you remove attacker persistence and validate a clean recovery point?
Rotate credentials/tokens and hunt for persistence
Rotate credentials and tokens, hunt and remove unauthorized remote access, repeatedly scan mounted snapshots until clean, and select known-good point.
Recover
Production systems are halted. Leadership demands recovery of ERP and shared file services within 7 hours to minimize business impact.
You must recover quickly—but safely—to make sure the attacker doesn’t return.

 Correct Answer
Correct Answer
Restore critical apps from a verified snapshot in a staged cutover. Validate with malware scans and smoke tests before going live. Fall back to your vaulted, immutable backup if needed.
 Incorrect answer
Incorrect answer
That decision backfired. Paying doesn’t guarantee data integrity and may violate policy or law.
 Neutral Answer
Neutral Answer
Full restoration without validation could reintroduce malware and extend downtime.
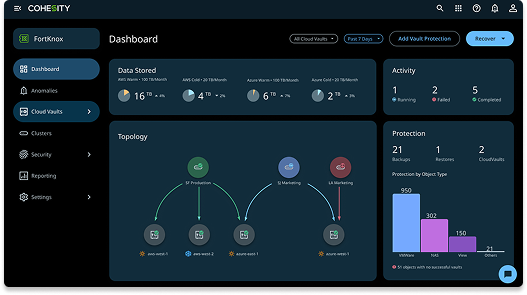
Confidently recover using an immutable copy of your data—even if primary backups are compromised or lost in a disaster.
Production systems are halted. Leadership demands recovery of ERP and shared file services within 7 hours to minimize business impact.
You must recover quickly—but safely—to make sure the attacker doesn’t return.
How will you recover business-critical data and services without risking reinfection?
Recover in stages and validate data integrity
Restore critical apps from a verified snapshot in a staged cutover. Validate with malware scans and smoke tests before going live. Fall back to your vaulted, immutable backup if needed.
Production systems are halted. Leadership demands recovery of ERP and shared file services within 7 hours to minimize business impact.
You must recover quickly—but safely—to make sure the attacker doesn’t return.
How will you recover business-critical data and services without risking reinfection?
Recover in stages and validate data integrity
Restore critical apps from a verified snapshot in a staged cutover. Validate with malware scans and smoke tests before going live. Fall back to your vaulted, immutable backup if needed.
Production systems are halted. Leadership demands recovery of ERP and shared file services within 7 hours to minimize business impact.
You must recover quickly—but safely—to make sure the attacker doesn’t return.
How will you recover business-critical data and services without risking reinfection?
Recover in stages and validate data integrity
Restore critical apps from a verified snapshot in a staged cutover. Validate with malware scans and smoke tests before going live. Fall back to your vaulted, immutable backup if needed.
Lessons Learned
A double-extortion attempt is confirmed—attackers threatened to leak stolen data on a Tor site if ransom demands weren’t met. Thanks to containment and a staged, secure recovery process, systems were restored without payment, and the incident was closed.
Let’s evaluate how your team responded and strengthen defenses for next time.

 Correct Answer
Correct Answer
Reinforce what you learned by updating recovery plans and clean room exercises. Preserve forensic evidence to inform future defenses and close access gaps.
 Incorrect answer
Incorrect answer
You’ve just destroyed valuable forensic evidence that could inform future defenses and compliance reporting. Preserve all evidence after every incident.
 Neutral Answer
Neutral Answer
Communicating lessons is good, but delaying improvements risks repeating the same mistakes.
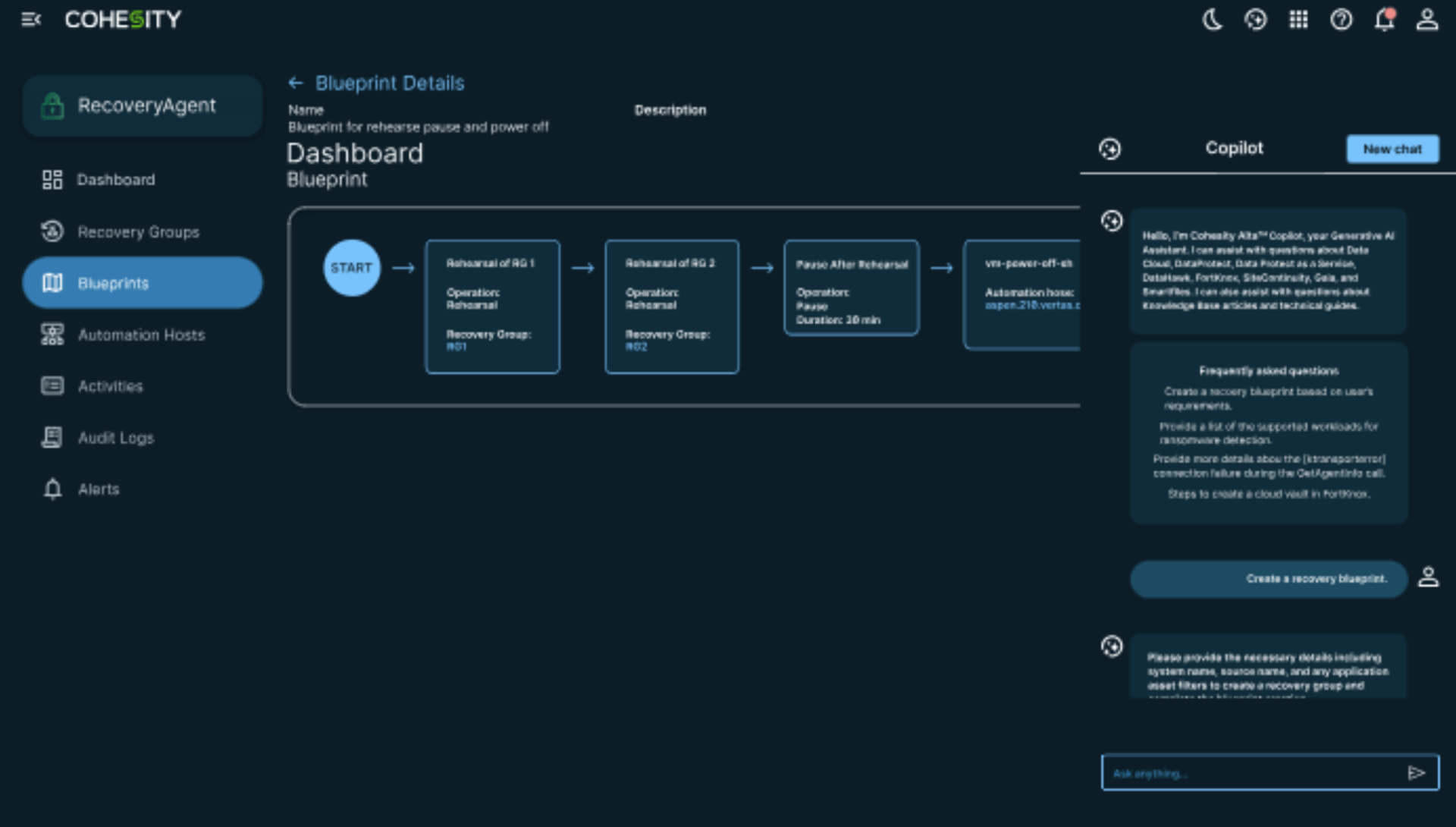
Rehearse, validate, and refine recovery strategies with blueprints that integrate critical steps like malware scanning and threat hunting.

Our expert-led assessments and tailored action plans help you stay ahead of today’s most advanced attacks.
A double-extortion attempt is confirmed—attackers threatened to leak stolen data on a Tor site if ransom demands weren’t met. Thanks to containment and a staged, secure recovery process, systems were restored without payment, and the incident was closed.
Let’s evaluate how your team responded and strengthen defenses for next time.
What did your post-incident review highlight?
Update recovery runbooks and schedule clean room drills
Reinforce what you learned by updating recovery plans and clean room exercises. Preserve forensic evidence to inform future defenses and close access gaps.
A double-extortion attempt is confirmed—attackers threatened to leak stolen data on a Tor site if ransom demands weren’t met. Thanks to containment and a staged, secure recovery process, systems were restored without payment, and the incident was closed.
Let’s evaluate how your team responded and strengthen defenses for next time.
What did your post-incident review highlight?
Update recovery runbooks and schedule clean room drills
Reinforce what you learned by updating recovery plans and clean room exercises. Preserve forensic evidence to inform future defenses and close access gaps.
A double-extortion attempt is confirmed—attackers threatened to leak stolen data on a Tor site if ransom demands weren’t met. Thanks to containment and a staged, secure recovery process, systems were restored without payment, and the incident was closed.
Let’s evaluate how your team responded and strengthen defenses for next time.
What did your post-incident review highlight?
Update recovery runbooks and schedule clean room drills
Reinforce what you learned by updating recovery plans and clean room exercises. Preserve forensic evidence to inform future defenses and close access gaps.


