Cohesity recently entered into a partnership with seven leading Data Security Posture Management (DSPM) vendors to help organizations increase resilience for their most critical data. In this blog, we explain how our technical integration with DSPM vendors works and why it matters.
Converging data security posture management (DSPM) and data protection
Cyber resilience requires that you are prepared for, and can recover from a cyberattack. First and foremost, you need visibility into your data estate—only then can you protect the “crown jewels” of your most important assets. This approach gives you a higher chance of recovery in the event of a cyberattack. Organizations that follow this best practice also enjoy many benefits, including significantly lower cyber insurance premiums.
To help increase resilience for your most critical data, Cohesity recently partnered with seven leading DSPM vendors including our long-standing partner BigID, as well as Cyera, Dig Security, Normalyze, Sentra, Securiti, and Concentric AI.
DSPM solutions provide visibility into known and forgotten data repositories across various cloud platforms, classify the data to identify sensitive information, and determine the risk of exposure for said data. DSPM helps you understand data usage, assess the security posture of the data stored, and comply with regulations.
For instance, a new rule from the U.S. Securities and Exchange Commission (SEC) requires all U.S.-listed companies to disclose cybersecurity incidents deemed “material” within four business days after the company determines it has experienced a cyber incident. In this rapidly changing landscape, knowing where your sensitive data resides and protecting them quickly is paramount.
Combining DSPM capabilities with Cohesity’s AI-powered data security and management platform helps you improve your security posture further across multiple clouds.
How the first implementation of the integration between Cohesity and DSPM solutions works
Let’s see how this integration works.
First, consider the example of a customer who uses Cohesity to protect their workloads relevant to high-priority or active business projects: virtual machines, databases, NAS, or M365. The backup administrator ensures that these important workloads are protected as part of the backup policy. But what about the data assets across multiple clouds that are NOT directly tied to these active projects but still contain potentially sensitive data assets?
Without a DSPM solution in place, these workloads can remain unidentified or forgotten and unprotected. And without that visibility, there can be gaps and inconsistencies in how the customer protects data.
In the above scenario, you have information on data assets that are included in a data protection plan, using the Cohesity solution. That’s a great place to be for many organizations.
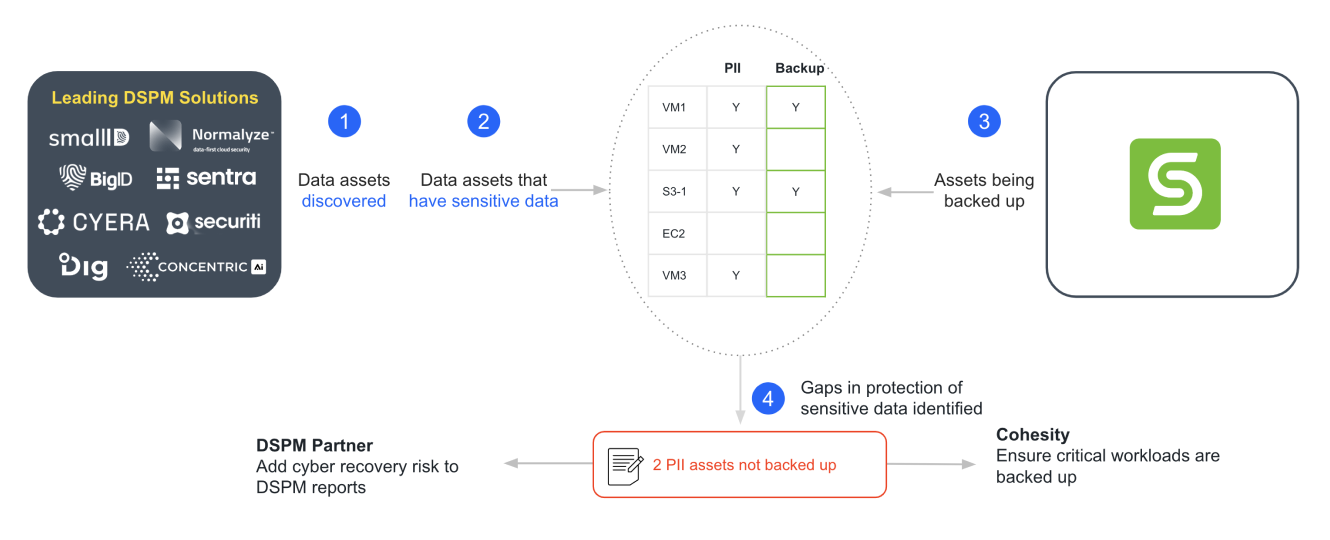
Now, complement Cohesity with a DSPM solution. You now have information on all cloud data assets, including in forgotten databases and shadow or unknown data repositories, and whether any sensitive patterns exist based on data classification, using the DSPM solution. This is shown below.
The integration between Cohesity and the DSPM solution merges this information. Following the above example, this connection uncovers two data assets with personally identifiable information (PII) that have not been backed up, much to the customer’s surprise.
The IT backup admin can now use the resulting reports to adjust data protection priorities and share the latest protection status with security teams. Security teams gain confidence in achieving their mandate of protecting certain data assets. Risk and compliance teams can benefit from this visibility to understand cyber recovery and compliance risks.
Benefits of the integration between Cohesity and DSPM solutions
Why are organizations like yours investing in DSPM, and then integrating it with Cohesity?
Here are three reasons:
- Discover sensitive data across cloud assets: Gain visibility into sensitive and critical data in your cloud infrastructure.
- Identify data protection gaps: Identify gaps in safeguarding your cloud workloads. Recognizing these gaps informs data protection priorities, ensuring that you can efficiently recover essential workloads when needed.
- Report on cyber recovery risk: By combining the capabilities of DSPM solutions with Cohesity, you can augment your assessment of data security posture with your ability to recover. This results in a more comprehensive understanding of cybersecurity risks and, as a result, more robust protection.
Cohesity and Normalyze integration is now generally available
We’re thrilled to announce that the integration with Normalyze, our initial design partner for DSPM integrations, is now generally available.
Customers who also use Normalyze can start using the integration in three easy steps:
First, configure the Normalyze app from the Cohesity dashboard.
- From the Cohesity dashboard, click the app-selector menu and click Security Center.
- In Security Center, select Integrations > Browse Integrations. You will see the list of all Cohesity-developed security integrations. Select Configure under the listed Normalyze application.
- Enter the API key and the API secret and click Configure.
Next, let’s take a look at this view in Cohesity.
- In Security Center, select Data Classification, and click Sensitive Data Posture.
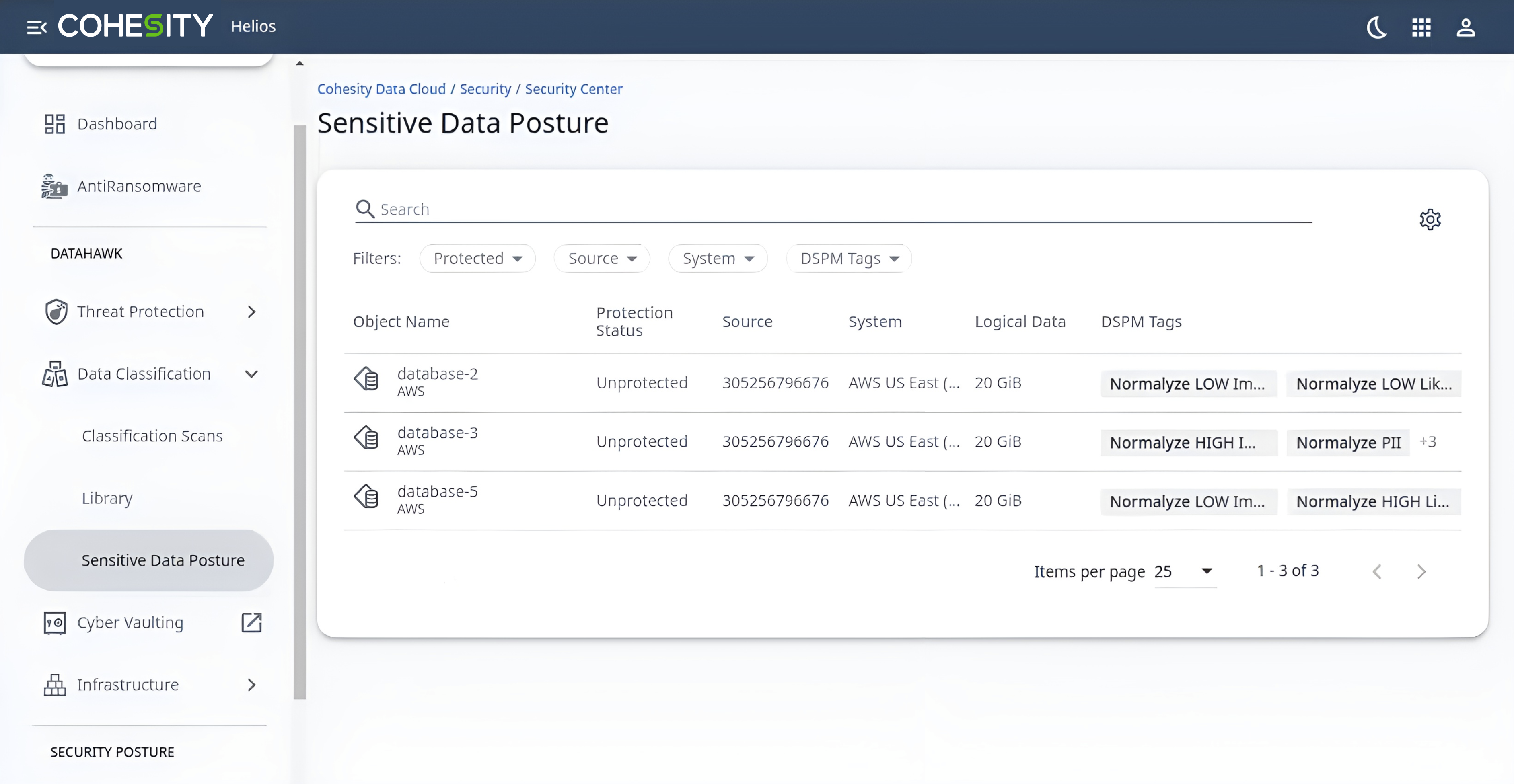
From this view, you can simply select the asset(s) that you want to protect, hit Protect, and select the appropriate protection policy for each.
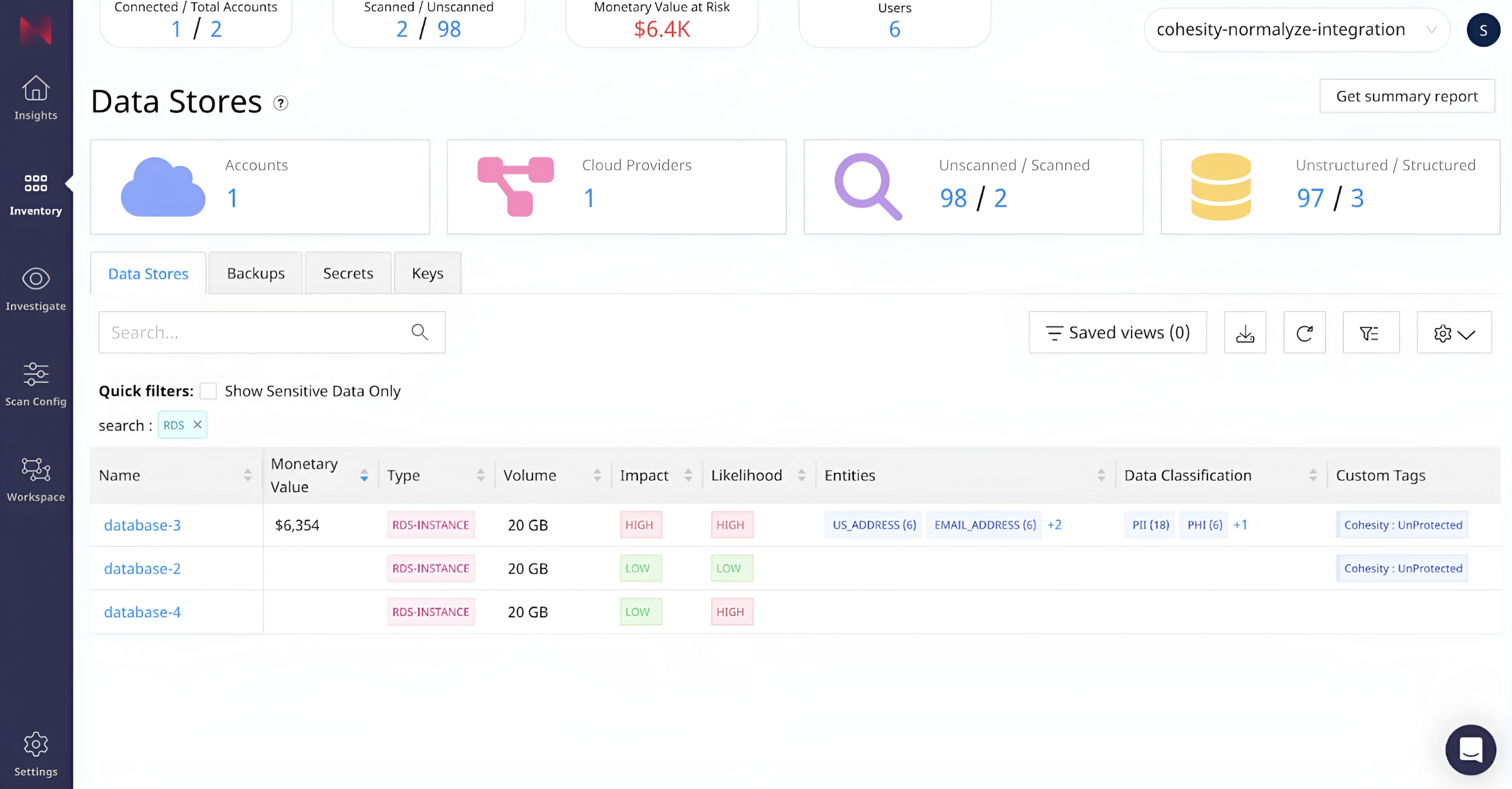
Now let’s see how the equivalent view looks from the Normalyze interface. In the inventory of data stores, Normalyze classifies the data in “database-3” as “PII” and “PHI”, and the integration delivers the protection status, which for this data asset is shown as “unprotected” in Custom Tags.
The consequences of limited visibility
The repercussions of limited visibility in cloud environments are far-reaching. A cyberattack can cripple an organization’s ability to conduct business, compromise sensitive customer data, and tarnish its reputation. Without proper data visibility, enterprises face difficulties in identifying the extent of a breach, reporting it to stakeholders, and taking timely remedial action. This significantly hinders their ability to recover from an attack promptly.
Learn more
To learn more about DSPM solutions and how our combined solution can enhance your security and cyber resilience, watch this Tech Insights conversation between Normalyze CEO Amer Deeba and Cohesity’s Shelly Calhoun-Jones. And stay tuned for upcoming integrations between Cohesity and our DSPM partners.



















%20%7C%20Cohesity&_biz_n=7&rnd=524730&cdn_o=a&_biz_z=1748210059878)
%20%7C%20Cohesity&rnd=185637&cdn_o=a&_biz_z=1748210059881)