
Have a conversation with your data
Power smarter business decisions—faster—with conversational AI.
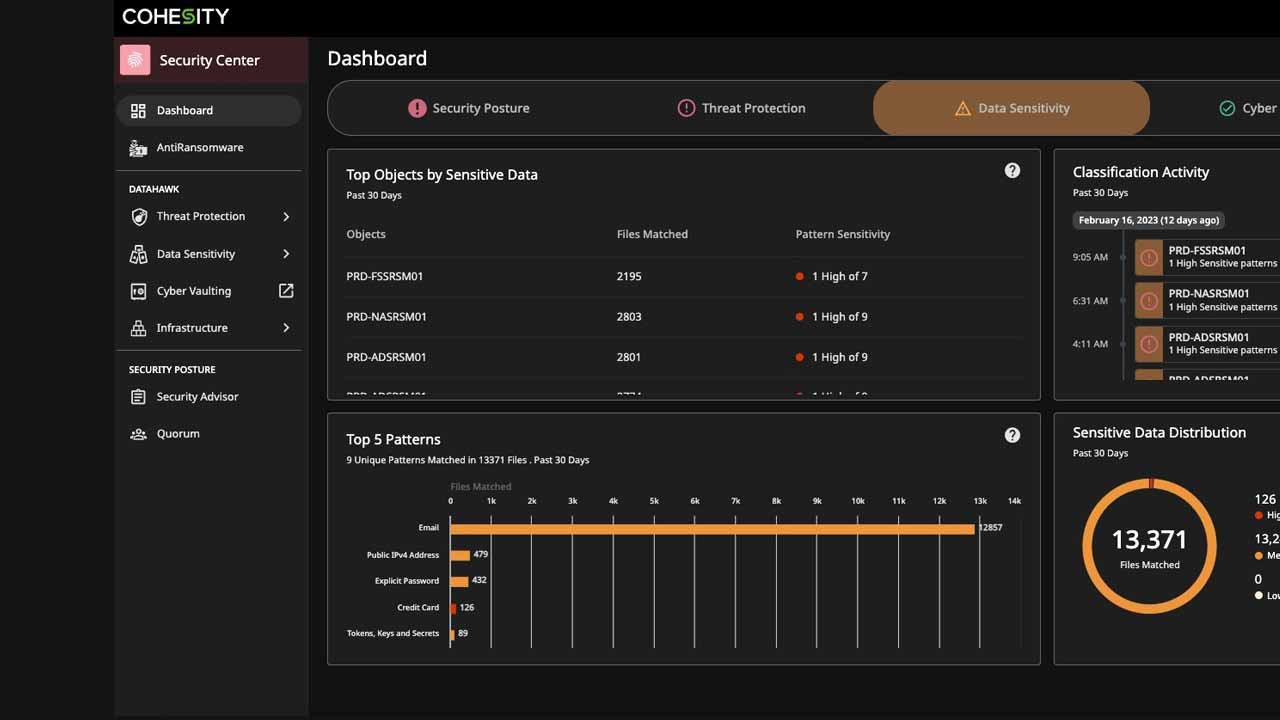
The Cohesity Security Center centralizes the management and response to ransomware and other threats that pose a risk to your data and your organization’s reputation. Thanks to its powerful dashboard and drill-down capabilities, you can leverage security posture monitoring, anomaly and threat detection, data classification, user activity tracking, and cyber vaulting—helping protect your organization’s data, detecting an attack, and recovering quickly without paying a ransom. See how the Cohesity Security Center gives you the visibility and control to manage today’s complex threats.
Stay one step ahead of cybercriminals with threat intelligence and scanning to identify elusive malware. Highly curated and managed threat feeds, trained with ML, always keep you up-to-date. Tailor threat detection and response to your specific needs by augmenting the extensive library of over 117,000 behavioral patterns. Create YARA rules defining indicators of compromise, or import custom rules. Support and simplify threat protection with 1-click threat detection at scale.
Find sensitive and regulated data and reduce false positives with ML-based data classification. Our highly accurate ML-based engine classifies sensitive data automatically or on-demand, including personal identifiable information (PII), PCI, and HIPAA. Organizations can understand their sensitive data for protection and security planning and rapidly assess the impact of a ransomware attack.
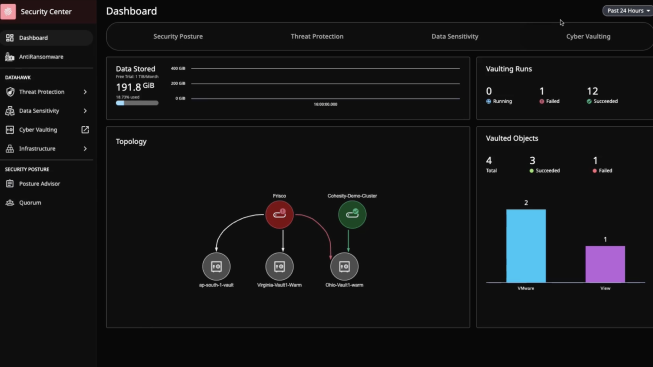
Enhance your data security against sophisticated ransomware attacks. DataHawk includes Cohesity FortKnox, a SaaS cyber vaulting and recovery solution that gives your data an additional layer of managed security and protection against cybersecurity threats. Simplify operations, lower costs, and recover confidently from attacks.
Securing your perimeter is not enough. Only Cohesity offers:
One platform for data security and data management
Data-centric intelligence using AI/ML to detect anomalies and threats
More protection from ransomware and other threats to cyber resilience
Security is a team sport. DataHawk integrates with leading perimeter and end-point security vendors, giving you greater visibility and actionable alerts in your Security Operations Center (SOC).



Ransomware protection encompasses traditional cybersecurity controls and helps ensure that backup data is safe and free from malware. It’s coupled with ransomware recovery so organizations can withstand and recover from attacks. Ransomware recovery allows for the restoration of data after an attack. When an organization refuses to pay the ransom for decryption keys, organizations can restore data that it protected to help restart business processes and services.
Key to protecting against ransomware is the ability to both withstand and recover from attacks. Traditional cybersecurity solutions provide capabilities to help withstand ransomware attacks. These include detecting unusual activity, locking down access to servers and endpoints, and having effective malware detection. Working hand in hand with cyber security, data security and management provides organizations with cyber recovery capabilities.This recovery allows organizations to refuse ransom payments and recover any affected data. In addition, cyber recovery solutions have a unique view of all of an organization’s critical data. This means recovery solutions can aid in thwarting ransomware attacks by detecting anomalies and threats in protected data and integrating with existing security operations and incident response.
The challenge with ransomware is not if, but when. The best cybersecurity efforts can be undone with a simple user error, such as clicking an attachment in an email. So organizations must have reliable recovery capabilities if they don’t want to pay ransomware operatives and have significant disruptions to their business operations. Plus, in order to qualify for cyber insurance coverage, providers now require robust recovery capabilities.