

Cohesity named a Leader again! 2023 Gartner® Magic Quadrant™ for Enterprise Backup and Recovery Software Solutions
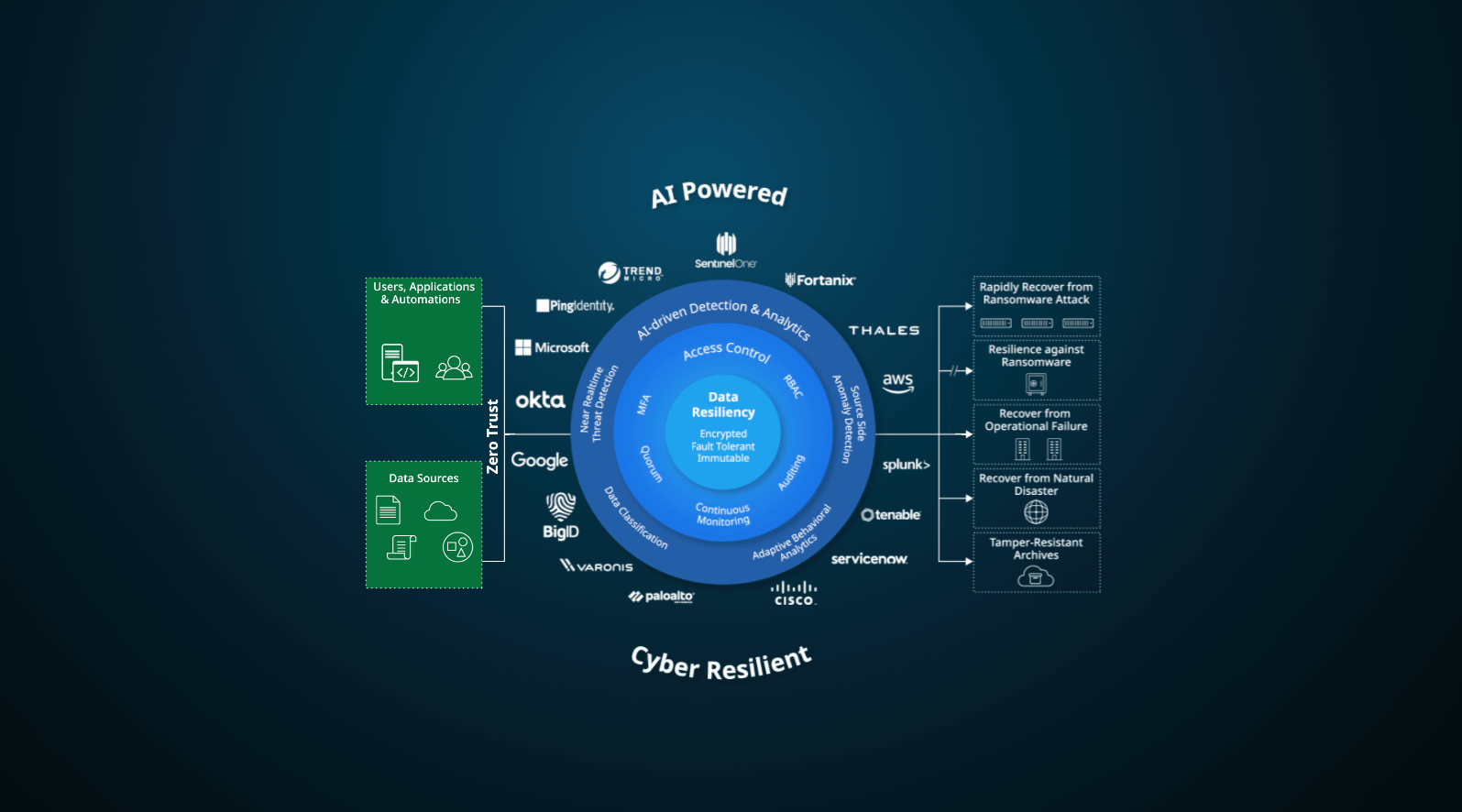
Protect your business from sophisticated ransomware attacks with a multilayered data security architecture.
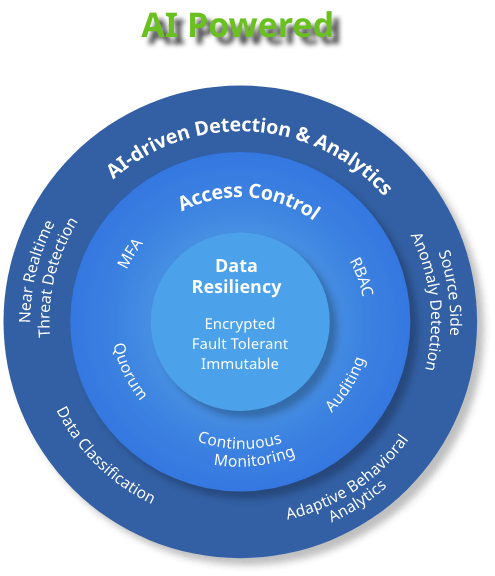
Protect your data, maintain strict access controls, and gain deep visibility in near real-time, to stay ahead of modern cybersecurity threats.
Defend your backup data from being taken hostage with a resilient architecture, including robust encryption algorithms, erasure coding, immutable backup snapshots, and WORM (DataLock).
Mitigate against the risk of weak or compromised user credentials with strict access controls like multifactor authentication, granular role based access control, Quorum, and more.
Minimize the risk of data exfiltration. Scan source-side production data and deploy Cohesity’s AI-powered advanced detection to reduce your blast radius.
Advance your security posture through leading integrations with cloud, data classification, end point, identity, and SIEM partners. Together, we’re helping to keep your data secure.
Backup is your last line of defense against sophisticated ransomware attacks. How robust is your backup product?