
Cohesity named a Leader again!
2024 Gartner® Magic Quadrant™ for Enterprise Backup and Recovery Software Solutions
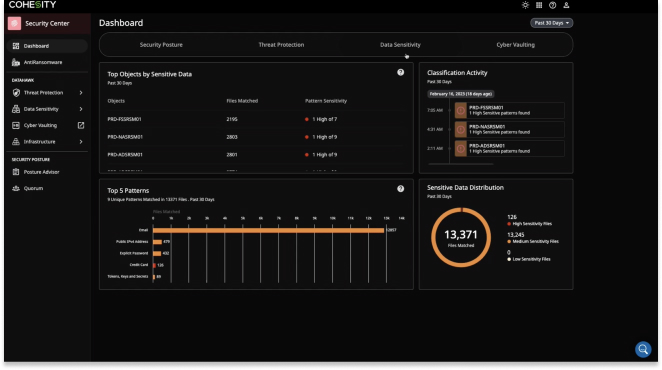
When ransomware attacks, do you know what sensitive data was affected? Classify sensitive data, including personal identifiable information (PII), using our highly accurate, ML-based engine. Understand sensitive data proliferation or invoke classification on anomalies for sensitive data impact analysis.
Go beyond regex pattern matching with our market-leading, ML-based classification engine. Use Named Entity Recognition (NER) and Natural Language Processing (NLP) techniques.
Get access to 235+ built-in patterns that cover all common personal, health, and financial data. Create custom policies to find sensitive data, and support regulatory and privacy requirements.
Understand attack impact fast, and save time by reducing false positives and negatives. Improve accuracy over time and get reliable, actionable results with ML/NLP-based training.
Knowledge is power—prepare for the inevitable. Uncover cyber risks and fortify your defenses now.

Data classification is the process of categorizing data based on its sensitivity, importance, or other criteria. This classification helps organizations manage and protect their data more effectively by assigning appropriate levels of security and access controls. Data classification helps ensure that sensitive or critical information receives the necessary protection, while less sensitive data may have fewer restrictions.
Data classification can vary based on the specific needs and requirements of an organization. However, some common types of data classification include:
Data classification is essential for compliance with regulatory requirements, such as GDPR, HIPAA, and PCI DSS, as well as for protecting sensitive information from unauthorized access, theft, or misuse. It also helps organizations prioritize their security efforts and allocate resources effectively based on the importance of different types of data.
Join Cohesity for a fully immersive 2-hour workshop created to simulate a live ransomware attack. Participants are invited to adopt the persona of a C-level decision-maker placed in the heart of ‘mission control’ of a fictional company.
