Benefit from resiliency at scale
Protect your data with immutability and hyperscale-inspired fault tolerance.
Boost cyber resiliency with ransomware recovery capabilities. Help enterprises identify, protect, and recover data and processes from sophisticated cybersecurity threats.
Protect your data with immutability and hyperscale-inspired fault tolerance.
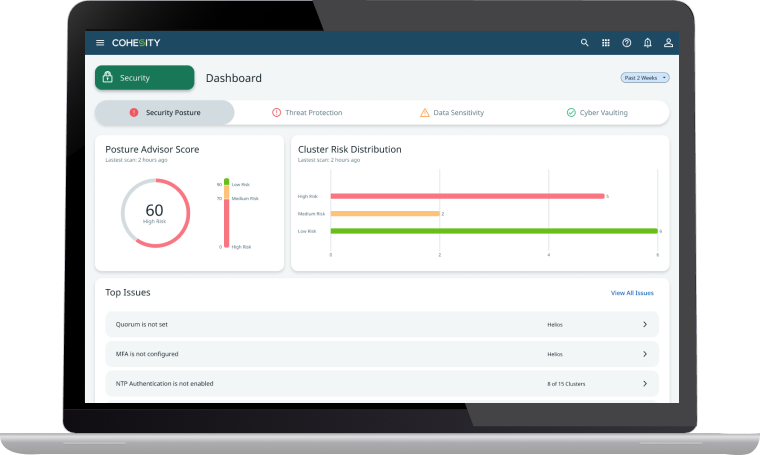
Advanced access controls—like MFA, RBAC, and Quorum—ensure you keep the bad guys out.
ML-based anomaly detection and threat scanning help identify threats so you can respond, remediate, and recover with confidence.

Enhance your cyber resiliency against sophisticated and evolving ransomware attacks. Cohesity FortKnox, a SaaS data isolation and recovery solution, gives your data an additional layer of security and protection against cybersecurity threats. Plus, it simplifies operations, lowers costs, and prepares you to recover confidently from attacks.
Simplify your response with automatic classification of data under attack. ML-based data classification helps discover and accurately classify sensitive data so you can determine the impact of an attack. User activity log analysis helps identify suspicious behaviors and activities that may be signs of tampering or theft.
Understand if cyber incidents may have exposed sensitive data and triggered compliance actions for GDPR, CCPA, PCI, and HIPAA by:
Recover at scale to any point and location. Cohesity helps reduce downtime and ensure business continuity after a ransomware attack.
Gain deep visibility and recover predictably. Avoid reinjecting malware or vulnerabilities in production while restoring.
Instantly recover hundreds of objects/VMs to any point in time using fully-hydrated snapshots and MegaFile.
Cohesity FortKnox provides a SaaS-based cyber vault with an immutable copy of data, providing an added layer of security against cybercriminals.
2023 Gartner® Magic Quadrant™ for Enterprise Backup and Recovery Software Solutions
Data security and management helps ensure that critical enterprise data is protected and secured to support recovery from cyber incidents—including ransomware, insider threats, and natural disasters. It also provides a secure central repository of mission-critical data for analytics, dev/test, and e-discovery.
Data security and management are foundational to cyber resilience and ransomware defense. Along with modern cybersecurity, they complete the cyber resilience equation, enabling organizations to not only withstand cyber incidents but to rapidly and effectively recover from them. Data security and management also provide a single, secure, and reliable data source for extracting value from an organization’s data.
Data security consists of four primary categories: (1) data protection, so organizations always have access to trusted copies of their critical data; (2) solutions such as encryption, tokenization, and masking, which obfuscate data from unauthorized viewing; (3) solutions such as Active Directory, multifactor authentication, and role-based access controls, which control access to data; and (4) solutions such as data loss prevention, UEBA, and file access monitoring, which help ensure data is used appropriately.
Concerns with data security relate to coverage, gaps, and compliance—to name just a few. Organizations may struggle to effectively protect and manage all workloads without multiple complex solutions. They may also have gaps in applying security controls, which creates risks for their security posture. Finally, organizations need to ensure their data security meets the requirements of privacy laws and industry regulations, such as GDPR, HIPAA and PCI.