Before you read this blog, let’s check off a couple of boxes to see if you’re my target market.
Did you check both? Brilliant. Keep reading. If not, keep reading anyway. There’s good stuff below.
What is the NIS 2 Directive?
Introduced in 2016, the Network and Information Security (NIS) Directive was the first piece of EU-wide cyber resilience legislation. The idea? Provide legal measures to uplevel the overall cybersecurity in the EU.
Now, it’s been revised and is referred to as the NIS 2 Directive. As a directive, each of the 27 EU member states will enact national laws by 17 October 2024 to enact the requirements of the directive. Some member states may choose to cover more sectors in its scope, or set additional requirements for those within scope, but the reality is the provisions of the directive will stand as a minimum requirement and should be used as a basis for organisations to plan and prepare.
Taking the steps needed to comply with NIS 2 will not only help organizations avoid costly regulatory fines but will also help them improve their data and cyber resilience.
NIS2 brings more industry sectors under its requirements
NIS 2 dramatically extends the scope of the original NIS Directive, bringing far more industry sectors under its requirements. In the table below, sectors covered by the 2016 NIS Directive are in black, while the new sectors covered by the NIS 2 Directive are highlighted in blue.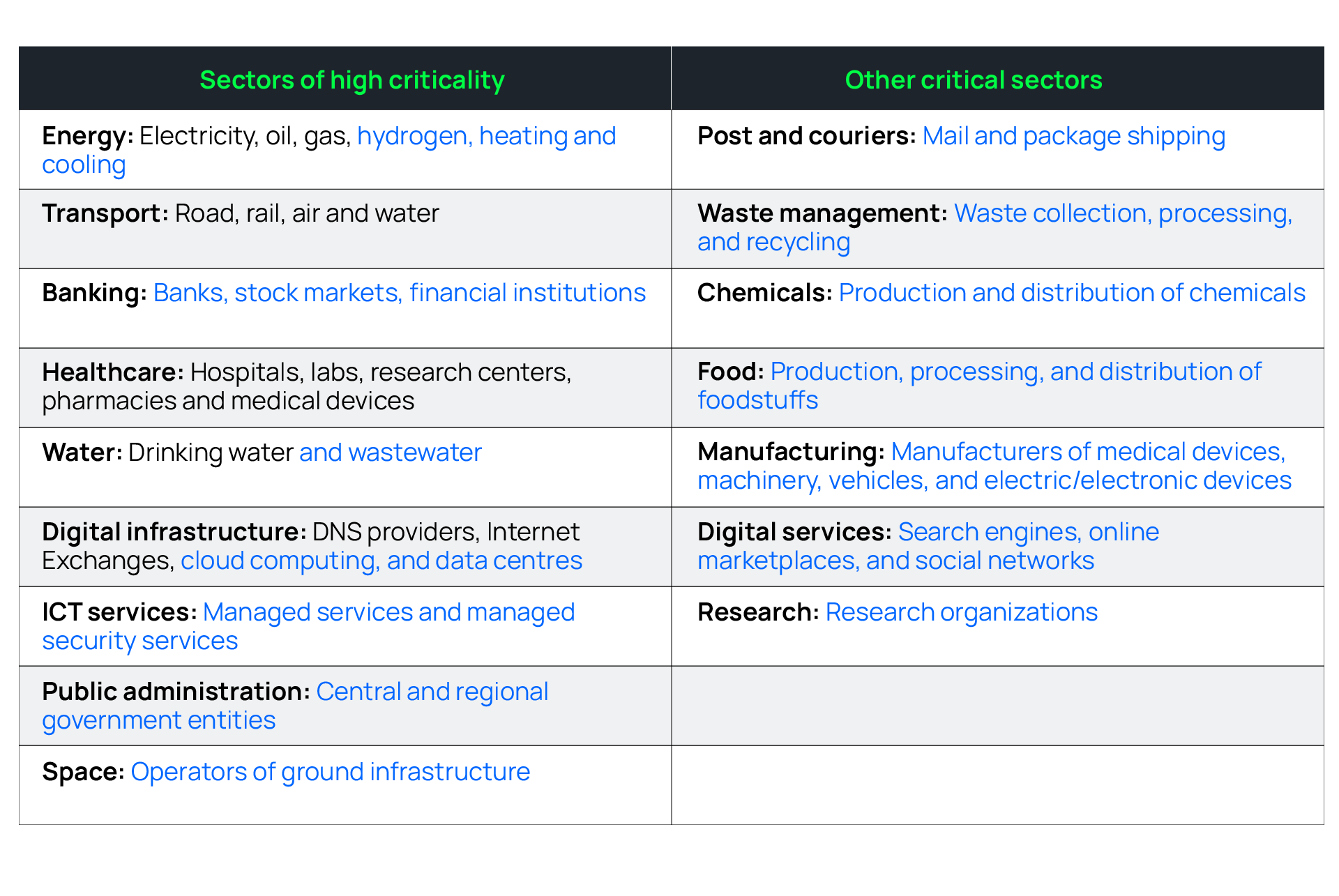
In NIS 2, similar to the provisions in the EU Digital Operational Resiliency Act (DORA) Regulation, providers of key Information & Communications Technology (ICT) such as search engines, cloud computing services, and online marketplaces, have also been brought into regulatory scope and will have to comply with the security and notification requirements under the directive. Local and national governments will also now find themselves subject to the provisions of NIS 2.
Breach notification reporting requirements
The second major change is the mandatory data breach notification reporting requirements of NIS 2. Under the directive, the following requirements are outlined:
- Within 24 hours, the organization must provide an early warning of whether a significant incident is suspected of being caused by unlawful or malicious acts or could have a cross-border impact.
- Then within 72 hours of becoming aware of a significant incident, the early warning needs to be updated with an initial assessment of the significant incident, including its severity and impact. The organization should also supply the national CERT with any indicators of compromise relating to the attack.
- If a national CERT or regulatory body requests it, the organization must supply intermediate status updates;
- Within a month of submission of the incident notification, the organization must supply a final report.
These breach notification and impact assessment requirements require organizations in scope to focus on understanding the data they have under management to assess potential reputational, operational, regulatory, and litigation impacts. They also require improving the effectiveness and efficiency of cyber incident response to achieve these mandatory timelines.
Article 21 of the NIS 2 Directive focuses on cybersecurity risk-management measures. It states that organizations must “take appropriate and proportionate technical, operational, and organizational measures” to manage the risks posed to the security of network and information systems and “… minimize the impact of incidents on recipients of their services and on other services.”
This Article describes the minimum level of measures as:
- Policies on risk analysis and information system security
- Incident handling
- Business continuity, such as backup management, disaster recovery, and crisis management
- Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers
- Security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure
- Policies and procedures to assess the effectiveness of cybersecurity risk-management measures
- Basic cyber hygiene practices and cybersecurity training
- Policies and procedures regarding the use of cryptography and, where appropriate, encryption
- Human resources security, access control policies, and asset management;
- The use of multifactor authentication or continuous authentication solutions, secured voice, video, text communications, and secured emergency communication systems within the entity, where appropriate
How Cohesity helps you comply with NIS 2
Cohesity’s data and cyber resilience capabilities can help organizations comply with these NIS 2 requirements, specifically:
Incident handling and risk management: Driven by both business prioritization and regulatory obligations, the priority in incident response is response activities. While many organizations may have Configuration Management Databases (CMDBs) that contain the details of the hardware and even Software Bills of Materials (SBOMs) in the modern world of hypervisors and cloud services, hardware and software are often commodities capable of being rebuilt or re-instantiated in seconds.
Data drives the business and enables the delivery of products and services. Data has the regulatory obligation to notify data subjects and regulators in the event of a breach. It is your data that the adversaries are targeting to steal, encrypt, or wipe.
Understanding your data, where it resides, and your regulatory obligations regarding that data is the starting point of any risk management strategy. The data classification capability of Cohesity DataHawk allows organizations to locate and classify their unstructured data as a part of their data and cyber risk management strategies, helping deliver operational resilience regardless of how an operational disruption manifests itself—whether a traditional business continuity scenario or cyberattack. DataHawk’s classification capability supports NIS 2’s requirement for Asset Management by allowing an organization to classify the impact of the data involved in the incident—even if the original systems are impacted by a cyber incident—allowing appropriate reporting to both the regulator and data subjects.
Unlike traditional business continuity and disaster recovery scenarios, cyber incidents require extensive investigation and threat mitigation before systems can be recovered. Investigation requires us to understand the attack by answering questions such as:
- How did the attack happen?
- What vulnerabilities were exploited?
- Which controls were missing or were circumvented?
- Which accounts were created or compromised?
- What persistence mechanisms were used?
- What is the availability of the security operations tooling to answer these questions?
- How can we communicate with customers, the press, our insurers, and law enforcement?
- Can we even gain physical access to the building that may have been impacted by the incident itself?
In these instances, you may need to restore your ability to communicate, collaborate, and respond before progress can be made.
Destructive cyberattacks often impact the core infrastructure, security tooling, and communications capability to start a response. Communication capability must be restored to allow the organization to engage with insurers, law enforcement, regulators, data subjects, business partners, and the media.
On top of this, traditional remote forensic imaging, threat hunting, and data classification solutions require network connectivity to function. One of the first actions in a destructive cyberattack is to contain the attack by isolating hosts and networks. Every second we delay response, our critical services are down. This is why Cohesity orchestrates the rapid recovery of a Clean Room, allowing these steps to get underway as soon as possible. Additionally, Cohesity snapshots can provide a view of filesystems across the incident timeline, allowing digital forensics teams to identify suspicious binaries and other changes to the filesystem.
Cohesity’s integration with our Data Security Alliance partners provides increased effectiveness and efficiency to a financial services institution’s existing Security Operations Center tooling, helping to reduce the time required for response.
Cohesity supports the NIS 2 requirement for Access Control Policies by providing granular role-based access control to achieve the security principle of least privilege. Quorum allows an organization to implement the security principle of separation of duties. Cohesity supports multifactor authentication and is built on Zero Trust principles for authentication. Encrypted communication protocols are used to provide secure communications, delivering even more of the stipulated NIS 2 requirements.
Business continuity and resilience testing
In addition to cyberattacks, organizations need to protect their diverse workloads across physical servers, hypervisors, and the cloud against traditional business continuity and disaster recovery scenarios to comply with NIS2. Cohesity DataProtect provides a proven rapid instant mass restore capability and Cohesity SiteContinuity allows the orchestration of interdependencies in recovery operations.
Cohesity provides support for resilience testing by supporting a customer’s automated testing of backups, as well as the continuous monitoring of the state of protection of systems.
You can increase your cyber resilience by ensuring that both your cyber response and recovery processes are efficient and effective. To learn more about cyber response, be sure to sign up for our ransomware resilience workshop.














%C2%A0%3F%20%7C%20D%C3%A9finition%20et%20avantages&_biz_n=0&rnd=936383&cdn_o=a&_biz_z=1752173443590)


