In February 2024, it’ll be a decade since the National Institute of Standards and Technology (NIST) released the original Framework for Improving Critical Infrastructure Cybersecurity (CSF). Despite its origins in the protection of U.S. critical national infrastructure, the framework has since been translated into nine languages. Seventy percent of cybersecurity leaders across all verticals see the framework as representing cybersecurity best practices.
When I led cyber risk management at the world’s largest bank and as the CISO of software as a service vendor that successfully listed on the NASDAQ, I heavily leaned on the Cybersecurity Framework as a foundation—even though my actual Information Security Management Systems were based around different control frameworks. I was lucky enough to have the opportunity to participate in both of the workshops organised by NIST to help shape the upcoming standard.
To reflect this broad adoption, version 2.0 of the Cybersecurity Framework changed the title and component text away from the original “Framework for Improving Critical Infrastructure Cybersecurity” to “Cyber Security Framework” and NIST has made several comments about wanting to make sure of the utility of the framework to organisations of all sizes, type, or vertical market.
Improved management of cyber risk
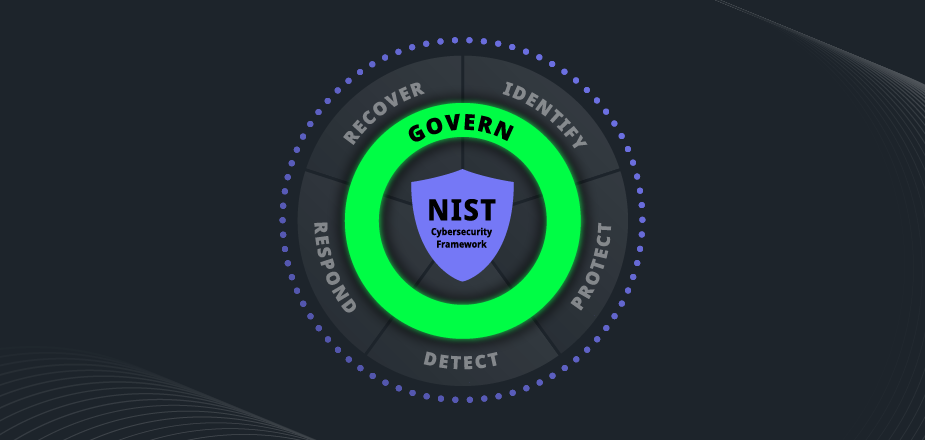
Many of the changes in version 2.0 of the Cybersecurity Framework align with a focus on improved management of cyber risk. The original Cybersecurity Framework had five functions: Identify, Protect, Detect, Respond, and Recover. Governance components were previously set inside of each of these functions, and with the advent of version 2.0 of the Cybersecurity Framework, a new Govern function sits as the bedrock of those previous 5 functions.
In addition, risk management used to sit within the Identify function, often giving the impression that cyber risk management is purely a periodic front-loaded activity, rather than the reality that decisions informed by risk are made continually throughout the incident lifecycle.
Although it existed in previous iterations, it’s worth calling out GV.RM-04: Cybersecurity risk management is considered part of enterprise risk management. Two of the five pillars of President Joe Biden’s National Cybersecurity Strategy are to shape market forces to drive security and resilience and invest in a resilient future. This recognition that in modern digitally-enabled organisations, cyber resiliency is a large part of operational, and even national resilience—is a welcome approach.
More mature organisations know that a myopic focus on prevention and detection rather than the removal of fragile and vulnerable artifacts while bolstering the ability to respond and recover is returning faster and cheaper risk mitigation dividends than the continual deployment of more likelihood mitigation tooling.
You’ve only got to look at the plethora of organisations with huge cyber security budgets and teams who have suffered ransomware incidents to realise that even with the best moats and walls around our organisations, adversaries just build better ladders and boats or just use metaphorical Trojan Horses to socially engineer our staff and waltz straight past all the barriers we put in place.
New risk management sub-categories
Several of the risk management aspects of the new Govern function already existed within the Identify function of the previous version, but version 2.0 of the Cybersecurity Framework brings several new risk management sub-categories that have been added to address the following:
- The strategic direction describing appropriate risk response options, including cybersecurity risk transfer mechanisms (e.g., insurance, outsourcing), investment in mitigations, and risk acceptance, is established and communicated (GV.RM-05).
- Responsibility and accountability are determined and communicated to ensure the risk management strategy and program are resourced, implemented, assessed, and maintained (GV.RM-06).
- The risk management strategy is reviewed and adjusted to ensure coverage of organisational requirements and risks (GV.RM-07).
- Organisational leaders assess and review the effectiveness and adequacy of cybersecurity risk management strategy and results (GV.RM-08).
Cybersecurity Framework Subcategories were always the most granular description of a risk mitigation outcome. In previous versions, each subcategory contained a description, but these are now augmented with a list of examples of actions that could be taken by an organisation to meet the CSF subcategory outcome. These examples help clarify the meaning and intent of each subcategory but are not meant to be a comprehensive list or a baseline to be measured against.
Increased focus on supply-chain risk management
Log4J was the vulnerability grinch that ruined Christmas 2021 for many of us in cybersecurity, and the SolarWinds breach showed how even the world’s largest organisations and the U.S. federal government can be attacked through the supply chain.
There is little wonder that there is an increased focus on supply-chain risk management in version 2.0 of the Cybersecurity Framework. One of the areas I’ve seen fall down in many organisations is misunderstanding the shared responsibility model in deploying the various flavours of cloud services, with customers making assumptions about the cyber resiliency tasks they still need to perform even after adopting cloud services. With the extension of the supply chain risk management category into the new Govern function, and its elevated importance in version 2.0, including the requirement to fully understand cybersecurity roles and responsibilities, this should lead to better cyber risk management outcomes for those adopting cloud services.
Cybersecurity Framework 2.0 has made improvements to the use of Implementation Tiers and Profiles. NIST has now provided an optional basic template for Profiles, providing a suggested format and areas to be considered in Profiles. It is hoped this will help develop and adopt threat, vertical market, and organisational-specific Profiles. Tweaks have been made to Implementation Tiers, which provide a mechanism for organisations to view and understand their cybersecurity risk approach and processes with increasing maturity, rigour, and sophistication. I’ve previously used Implementation Tiers as a way to measure and communicate the maturity of my cybersecurity programs, and Cybersecurity Framework 2.0 adds clarification to the scope and applicability of Implementation Tiers with regard to the robustness of an organisation’s risk management processes, programs, and external communications.
The Cybersecurity and Privacy Reference Tool (CPRT)
Alongside the Cybersecurity Framework 2.0, NIST also announced the Cybersecurity and Privacy Reference Tool (CPRT) available in Excel and a machine-readable JSON schema allowing organisations to identify, locate, compare, and leverage content from the interrelated NIST resources to build their own cybersecurity and privacy management system.
Remembering that NIST Cybersecurity Framework ultimately provides Informative References that link back to other popular control frameworks like ISO 27001/27002; NIST SP500-83, ISACA COBIT 5.0, and the Center for Internet Security’s Critical Security Controls (CIS CSC), this provides a rich resource to tie together cybersecurity and privacy approaches, regardless of the underlying control framework your organisations has been historically aligned to.
The importance of risk governance
At the end of the day, NIST Cybersecurity Framework 2.0 isn’t a radical reworking of previous versions. Instead, it is a natural progression reflecting the need for increased focus on risk governance and the changes in how we deliver our IT services, and it will continue to be a go-to resource for many of us who are aligning our strategic cyber security initiatives with enterprise risk and ensure that our operations continue to deliver value to this strategic aim.
Further reading: