Did you see the recent news on Qakbot? After a decade and a half in the wild, it appears that U.S. authorities finally took down a network that infected hundreds of thousands of computers and caused millions of dollars in damages.
It reminds me of a memorable Christmas Eve I had about a decade ago. It wasn’t the most wonderful time of the year. The company I was working with at the time was dealing with a virus outbreak during their busiest time of year. This meant working over the holidays to get the environment cleaned up.
It was a polymorphic threat, meaning it wasn’t easily detectable by their endpoint security and actively spread through network shares. We deployed some configuration changes and custom threat signatures from the security vendor.
At the time, threat hunting was a relatively new concept. But a year later, Virus Total created an open-source tool called YARA to help companies hunt for threats in their environment. YARA stands for “Yet Another Recursive Acronym” and security professionals use this tool to identify and classify malware.
Hunt for threats using YARA rules
For my customer, having custom YARA rules—like one based on a threat artifact—would have sped up the threat-hunting process. A threat artifact is a file left over from the infection which indicates compromise. A threat artifact could be a PDF file used in a phishing attack with a link to a malicious website or files damaged by ransomware. But you can also create YARA rules based on other types of Indicators of Compromise (IOCs), which act as breadcrumbs, to detect malicious activity early in the attack sequence.
IOCs can be network-based and seen by monitoring traffic, such as traffic communicating with a malicious domain or suspicious IP address. You can also detect IOCs by observing behavioral patterns in event logs, such as many failed login attempts or abnormal system activity. File-based IOCs are typically associated with a specific file name (like encryptor.exe) or a file hash. You can use this information to understand how the threat infiltrated the environment and refine your security policies.
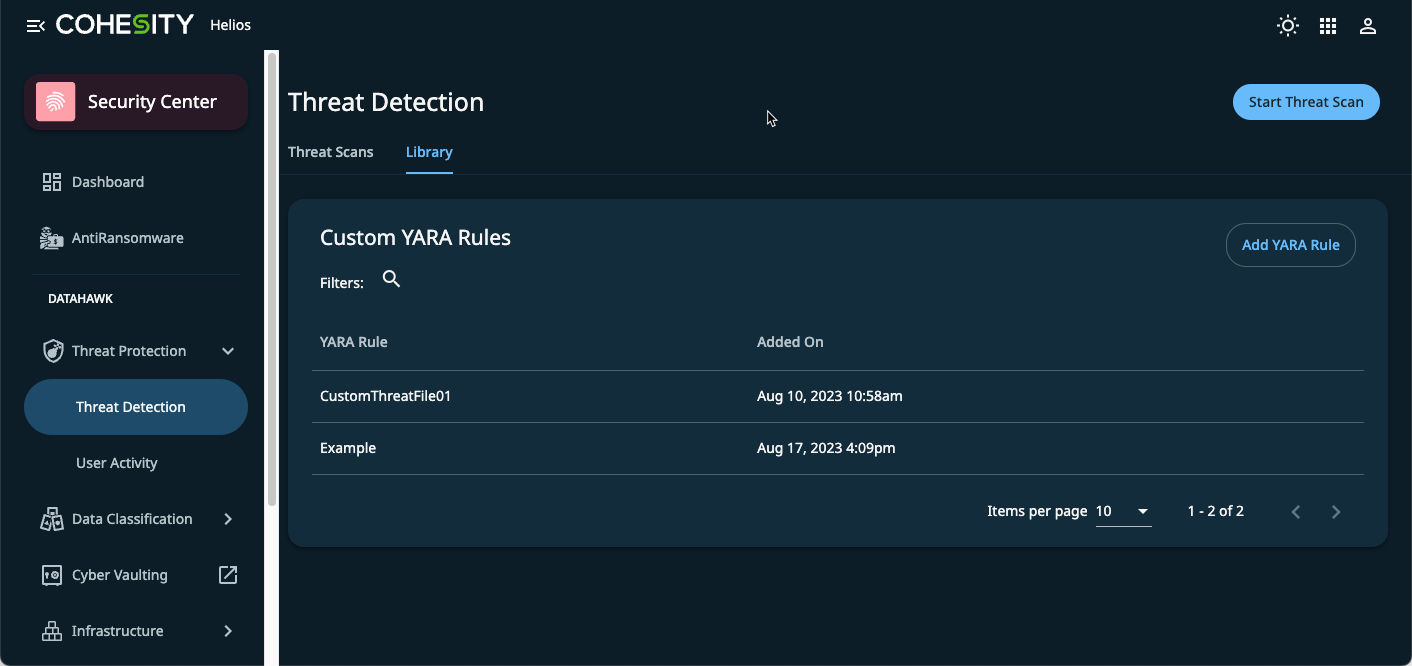
Cohesity DataHawk now supports YARA rules and provides pre-packed IOCs called a Default Threat Library. In addition to the Default Threat Library, you can also use custom YARA rules when performing threat detection scans on your vSphere VM snapshots.
You can access this feature in the Cohesity Security Center in Threat Protection > Threat Detection. Select the Library tab and click Add YARA Rule. You can also learn more about adding YARA rules in this Cohesity article.
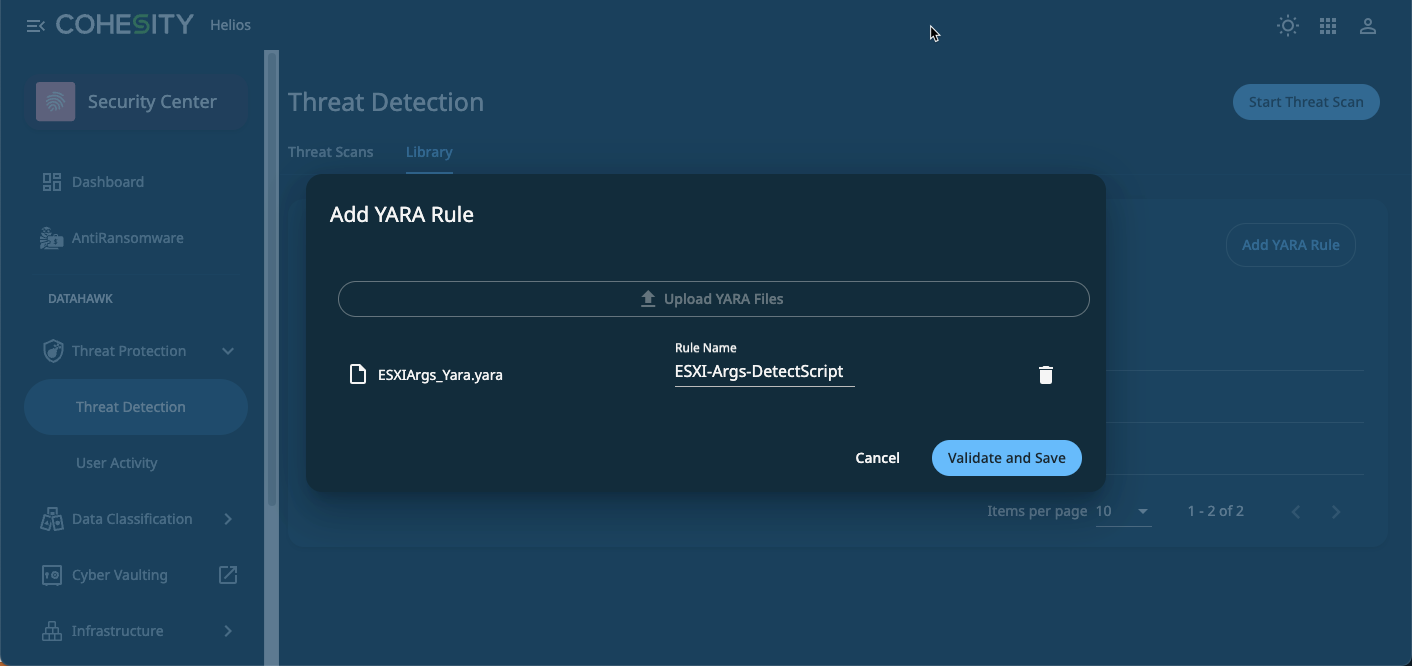
YARA rule example
In the example below, I’m importing an ESXiArgs YARA rule from Cloudsek. You can also reference Awesome YARA rules on GitHub for more examples of how to get started with YARA rules.
After adding the new YARA rule, you’re ready to run a Threat Detection scan. In this example, I’m running a scan on my SCJ-Server workload. You’ll also notice that I’ve also chosen to use the Default Threat Library which includes built-in IOCs that the Threat Detection Scan will use to scan the workload. Read this Cohesity article to learn more about how to run Threat Detection scans on workloads.
Whether investigating with an active security event or proactively improving your cyber resilience, YARA is a powerful tool. (Having YARA rules would have been the perfect holiday gift for my customer years ago.) You can use it for identifying and classifying malware and creating advanced rules to detect new threat variants. After testing, you can deploy it to your security products and Cohesity DataHawk to scan your vSphere VM snapshots. It helps keep your environment secure and minimizes the impact of a ransomware attack.
I’ve also recorded a video which can help get you started. You can watch it below. It shows how to:
- Review an anomaly within the Cohesity Security Center
- Perform a threat detection scan
- Review an existing threat detection scan
- Analyze a suspicious file on Virus Total
- And, how to import a YARA rule into DataHawk