I live in Oregon, and we deal with forest fires every year. As a homeowner with forested property, I’ve taken proactive measures to make our land fire-resistant, but I also have a plan of what to do if a fire encroaches on my land. The same thinking applies in the security world—the goal is to use a defense-in-depth approach to secure your assets and ensure you have the right tools to respond to an active security event.
Fighting digital fires with automated playbooks
The challenge for security operations teams is ensuring that you have the correct visibility into emerging threats and the ability to quickly respond to incidents. It’s like dealing with a fire. You assess the situation, secure your assets to minimize damage, and fight the fire. Then, after containing it, you’re ready to investigate and figure out what happened. The same applies when responding to a security event, and for this, organizations use SOAR (Security Orchestration, Automation, and Response) platforms for rapid triage.
But how does this play out from a backup and recovery perspective? Most companies manage their backup and security operations teams in different parts of the organization. If you’re a security operations person dealing with a new incident, you will likely have access to a different set of tools than your backup operations team. On that note, it’s essential to have someone who understands the process from beginning to end, from incident awareness to recovery.
Cohesity integrates with Microsoft Sentinel using playbooks. Microsoft Sentinel playbooks help you schedule, automate, and orchestrate tasks and workflows across your environment. For example, you may require that a notification be sent to a Microsoft Teams channel and synced to another ticketing system when a new security event occurs. Once in the new ticketing system, other team members can triage and gather evidence. For example, your organization could be dealing with a new threat variant, and you need to analyze the threat. But from a backup and recovery perspective, you also need to monitor your snapshots for abnormal changes in your data. Abnormal changes can indicate compromise as threats like ransomware not only blocks access to files, but the infection can also download files and other malware from a command-and-control server or perform data exfiltration.
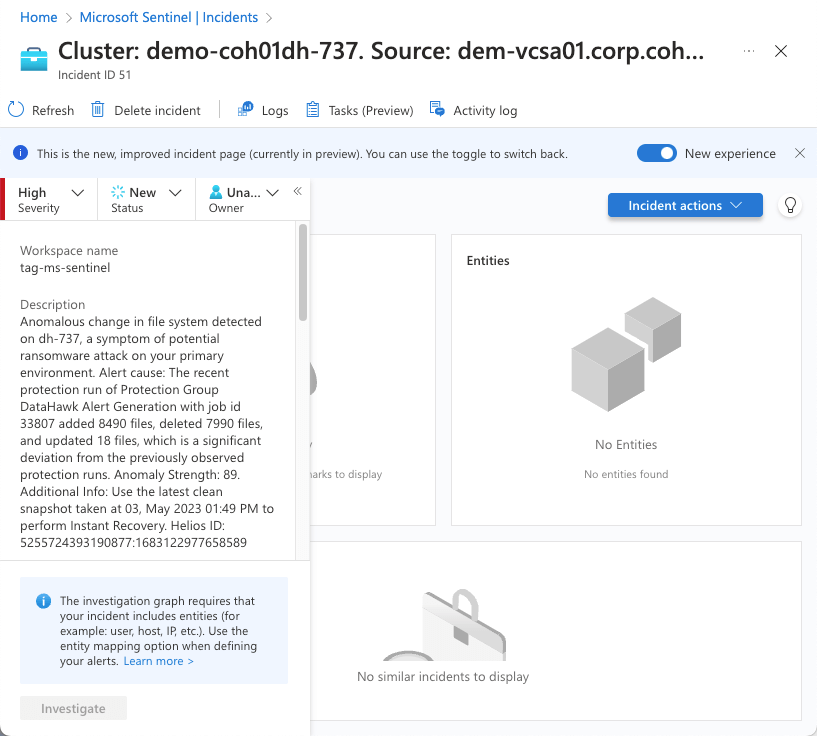
After enabling the Microsoft Sentinel integration, notifications from Cohesity will appear as a new incident in Microsoft Sentinel. In the Cohesity platform, these notifications appear in the Security Center under AntiRansomware as Objects with Anomalous Snapshots. See the image below.
In this screenshot example above, the alert recommends recovering using a clean snapshot. However, there may also be other tasks that you need to perform, such as opening a ticket in a helpdesk system, or you may need to gather evidence from the compromised server.
When a new incident appears, you can take ownership and view the incident details, like in this example. In addition, it’ll provide information about the impacted server and a recommended action plan.
When I need to act, I can run the appropriate playbooks:
- My_Cohesity_Restore_From_Last_Snapshot: Recover a clean snapshot for the impacted server.
- My_Cohesity_Send_Incident_Email: Send an email notification to an individual or distribution list.
- My_Cohesity_Close_Helios_Incident: Close the incident in Cohesity once the recovery is complete.
You can find these playbooks and more under Incident Actions > Run Playbook in Microsoft Sentinel.
Watch my demo of the Microsoft Sentinel integration with Cohesity below.
Build your security triage workflows
Most organizations have specific processes and procedures that you use for responding to a new security event. Microsoft Sentinel gives you the ability to create your custom workflows. Microsoft provides examples that you can access via Microsoft Learn and GitHub. After setting up your playbooks, you can run them manually or automatically. Some organizations prefer a hybrid approach, allowing security operations personnel to act on specific threat actors on demand, but automating other workflow elements. Another example will be if your team creates a new set of playbooks that you must test before deploying them in automation rules.
The first line of defense is preparation
Whether it’s a forest fire or dealing with a new threat, the first line of defense is preparation. Preparation allows you to document and understand your organization’s policies and procedures for incident response. It also allows you to configure your environment, detect suspicious activity, educate your teams, and proactively use threat intelligence feeds to identify malicious activity. If you do run into a security event, having the ability to respond quickly and get back online is essential.
Playbooks are part of that process and can help with containment and recovery. You can use information from the incident in a future “lessons-learned” session with your team to understand how and why it happened. Finally, you can use the data from the lessons learned session to fine-tune your security policies and incident response procedures. The threat landscape continues to evolve and with that, the need for robust security.
For more information:
- The Cohesity Security Integration for Microsoft is available at both the Cohesity Marketplace and the Azure Marketplace.
- Learn how to automate threat response in Microsoft Sentinel.
- Access playbook templates via the GitHub repository.
This blog is part of our “Road to Catalyst” series. Check back every week for new data security and AI content, and register today to join us at Cohesity Catalyst, our data security and management virtual summit.