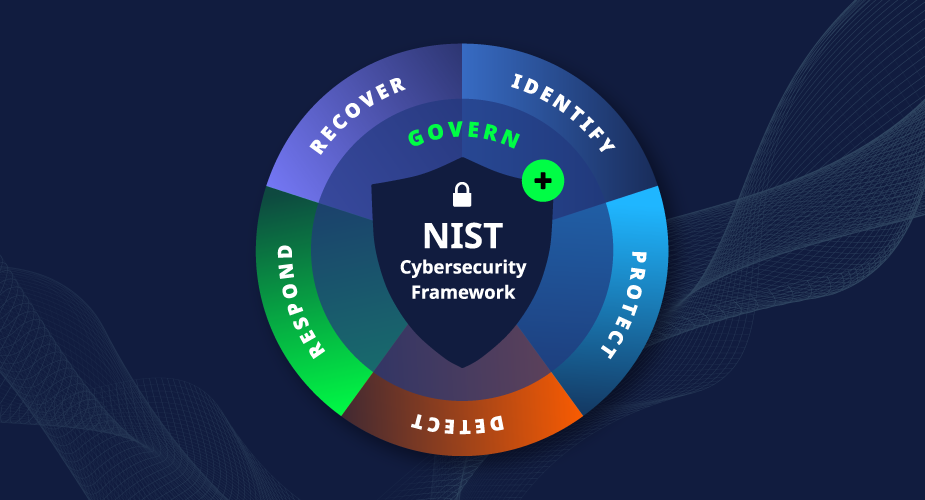
The NIST Cybersecurity Framework is getting its first makeover in almost a decade.
The National Institute of Standards and Technology (NIST) recently announced an additional pillar to its cybersecurity framework. The new term “govern” will join the version 1.1 pillars: identify, protect, detect, respond, and recover.
Cybersecurity continues to be top of mind for IT pros as ransomware, wipers, and other threats continue to pose serious concerns for enterprises. So when NIST put out a February 2022 request for information, respondents suggested that an update could help users adjust to tech innovation as well as the rapidly evolving threat landscape.
“With this update, we are trying to reflect current usage of the Cybersecurity Framework, and to anticipate future usage as well,” said NIST’s Cherilyn Pascoe, the framework’s lead developer.
What are the changes to the Cybersecurity Framework (CSF)?
The draft version of the CSF 2.0 updates the tool first released in 2014 to help organizations understand, reduce, and communicate about cybersecurity risk.
There are three significant changes:
- Change #1: Though the CSF was developed for critical infrastructure, this update now shifts the focus from critical infrastructure to everyone. “We want to make sure that it is a tool that’s useful to all sectors, not just those designated as critical,” said Pascoe. This updated thinking is seen in the CSF’s official title, “The Cybersecurity Framework.” Its previous title was a bit more limiting, “Framework for Improving Critical Infrastructure Cybersecurity.”
- Change #2: Adds a new pillar, govern, rounding out the main functions of a successful and holistic cybersecurity program. “Govern” covers internal decision-making and how to implement those decisions.
- Change #3: Adds profiles to improve and expand guidance on implementing the CSF and help tailor the CSF to particular use cases. The CSF 2.0 draft now includes implementation examples to help organizations use the framework effectively.
The current state of data security and management
A typical ransomware payload aims to render your most critical business assets useless by encrypting, destroying, or otherwise disrupting access to data. Bad actors do this in hopes of extorting a ransom payout.
In recent years, these attacks often have involved the stealing, leaking, and exfiltration of sensitive data. This can make desperate organizations more prone to consider paying to avoid disruption and harm to their business reputation. Given the increasingly sophisticated tactics used to attack business data, it’s important to stay ahead of these malicious actors with a comprehensive approach that can not only protect the data itself but also ensure that businesses suffer minimal loss and can recover quickly from attacks.
With the global workforce distributed across on-premises, edge, and cloud locations, properly safeguarding enterprise data at scale against cyber threats like ransomware is not just about protection and recovery. It’s also important to consider other functions like identification, detection, and response.
How Cohesity aligns with the CSF
Cohesity delivers AI-powered data security and management to combat cyber threats and keep your data secure and compliant. We do this via the Cohesity Data Cloud, our platform for securing and managing enterprise data, no matter where it lives. See below for details on how Cohesity solutions align with the NIST functions.
- Identify: Quickly discover and classify sensitive data with AI/ML-trained behavior patterns and up-to-date threat intelligence feeds with Cohesity DataHawk.
- Protect: Safeguard your data against emerging cybersecurity threats with unlimited immutable snapshots, Zero Trust Security principles, role-based access controls, powerful encryption, multifactor authentication, and more.
- Isolate your backups with a virtual air gap in an immutable cloud vault, Cohesity FortKnox, for an extra layer of protection against ransomware with rapid recovery to any location or cloud.
- Detect: Automatically detect the latest threats, ransomware variants, and anomalies in your backup data so you can accelerate recovery with clean data and great confidence.
- Respond: Accelerate responses to ransomware attacks and other security incidents with user behavior monitoring, audit logging, and reporting capabilities of the Cohesity Data Cloud.
- Recover: Exceed SLAs and get users and applications back to business right away—while data is seamlessly restored to production locations in the background—with near-instant recovery capabilities.
Bringing the NIST framework to life
We believe security is a team sport. So we’ve been building out a world-class data security ecosystem—the Data Security Alliance—with leaders in data security, response, and remediation. Our deep integrations with cybersecurity leaders including Palo Alto Networks, CrowdStrike, NetSkope, zScaler (available in the coming months), and more, bring best-in-breed security innovations to your data to ensure that your mission-critical business assets remain protected. We’re also committed to aligning with the NIST framework.
Our vision for security is simple. Build out a deep ecosystem to help you manage risk to data. And work with the solutions you already use today. By focusing on these integrations and partnerships, we help bring the NIST Cybersecurity Framework to life.