Many organizations face two primary threats in the age of ransomware attacks: malicious actors and a lack of preparedness. In a recent survey, over 90% believe the threat of ransomware attacks increased in 2023. And yet, 80% of organizations fear their cyber resilience strategies aren’t enough.
Growing data silos and multiple point solutions for data protection contribute to the growing complexity for response and recovery planning. In the event of a cyberattack, a lack of consolidation makes it even more difficult to assess the impact of an attack and mitigate risks before initiating recovery.
With Cohesity, customers can sustain critical business operations and minimize impact during a cyber event with a consolidated cyber resilience solution to protect critical business data, detect anomalies and impact, quickly and efficiently respond to a cyberattack, and safely recover business data at scale. A key component to cyber resilience at scale is our data security solution, Cohesity DataHawk.
Improve cyber resilience amidst growing cyber threats
Cohesity set out to make data security and management simpler. Cohesity’s AI-powered modern data security and management solution consolidates data protection with threat intelligence into a single platform. The result is that in the event of a cyberattack, organizations have global visibility into data assets and can more easily align resources for a safe and quick response and recovery. With Cohesity, organizations can:
- Improve threat detection: Find threats, anomalies, and exposure of sensitive data across your data to reduce the risk of an attack or data loss.
- Safely respond and recover: Securely and confidently respond and recover to attacks by isolating critical data.
- Improve security efficiency: Reduce the risk of impact from a cyber event with automated security operations across your security suite and deep SOC and security ecosystem integrations to improve your security posture.
We’re excited to announce substantial updates to DataHawk that will further support cyber resilience strategies at scale, including expanded threat intelligence support for NAS, new risk mitigation dashboards, and sensitive data exfiltration protection with Zscaler. Read on for the latest updates over the last few months.
Improve threat hunting
Cybercriminals will stop at nothing to find and exploit any vulnerability in your data environment. Proactive threat hunting, continuous monitoring of data changes, and detecting anomalies are critical for minimizing the impact of an attack. Cohesity is excited to announce the broad expansion of threat intelligence capabilities that boost cyber resilience:
- New critical data workload support for data classification and threat intelligence: Since Cohesity launched DataHawk over a year ago, we have invested extensively in advanced data security capabilities for critical data sources like virtual machines, and turn-key integrations with key security solutions like leading SIEM and SOAR providers, threat feeds, and DSPM vendors, to name a few. Now organizations can use these critical cyber resilience capabilities on NAS data sources such as NetApp and Isilon. These exciting updates enable organizations to easily classify sensitive data on backup snapshots from NAS, NetApp, and Isilon, and reactively and proactively hunt for threats.
- On-demand data classification: Cohesity AI-based data classification engine enables organizations to proactively identify and classify sensitive data at scale, such as personal identifiable information (PII) to streamline compliance and governance operations for PCI, HIPAA, GDPR, and more. Knowing where critical data is helps to prioritize response activities. Now organizations can initiate on-demand data classification to better understand the impact to sensitive data in the event of a cyberattack.
- Threat hunting with imported YARA rules: Cohesity’s threat hunting capabilities help to find elusive threats using AI-driven threat detection that identifies the latest variants of ransomware and other cyberattacks. Our extensive library of over 117K threat rules is updated frequently with the latest threats. Now organizations can enhance threat-hunting capabilities by importing custom YARA rules.
Check out our expert-led demos for DataHawk to see these capabilities in action, or view a video of custom YARA rules below.
Safely respond and recover
A key benefit for Cohesity customers is having a single management plane across all data, regardless of where it resides. Backup data in self-managed on-prem or virtual clouds, in addition to Cohesity-managed data protection workloads in AWS or Azure, has a single interface for managing data, applying policies, and sharing services.
Our cyber resilience solutions include a Security Center to consolidate security intelligence and command into an integrated dashboard to monitor security alerts, threats, sensitive data exposure, data isolation status, and the security posture of the Cohesity platform. The security center provides drill down and control to all DataHawk capabilities to manage platform health and threats—and control security settings and schedules.
Preparedness is the first step to improving response and recovery in the event of a cyber attack. With new dashboards that improve visibility into key risk factors like malware detection and whether data is backed up or isolated, organizations can improve cyber resilience and minimize impact in the event of an attack. New capabilities include:
- New Security Center Inventory view to mitigate risk: The new dashboard offers a single view for assessing cyber risks for all key workloads, including identifying whether data is backed up and protected by Cohesity, surfacing anomalies or known threats, and whether data is isolated in a virtual air-gap environment. If data has not been scanned for threats or for identifying sensitive data, users can launch on-demand data classification or threat scans directly from the dashboard.
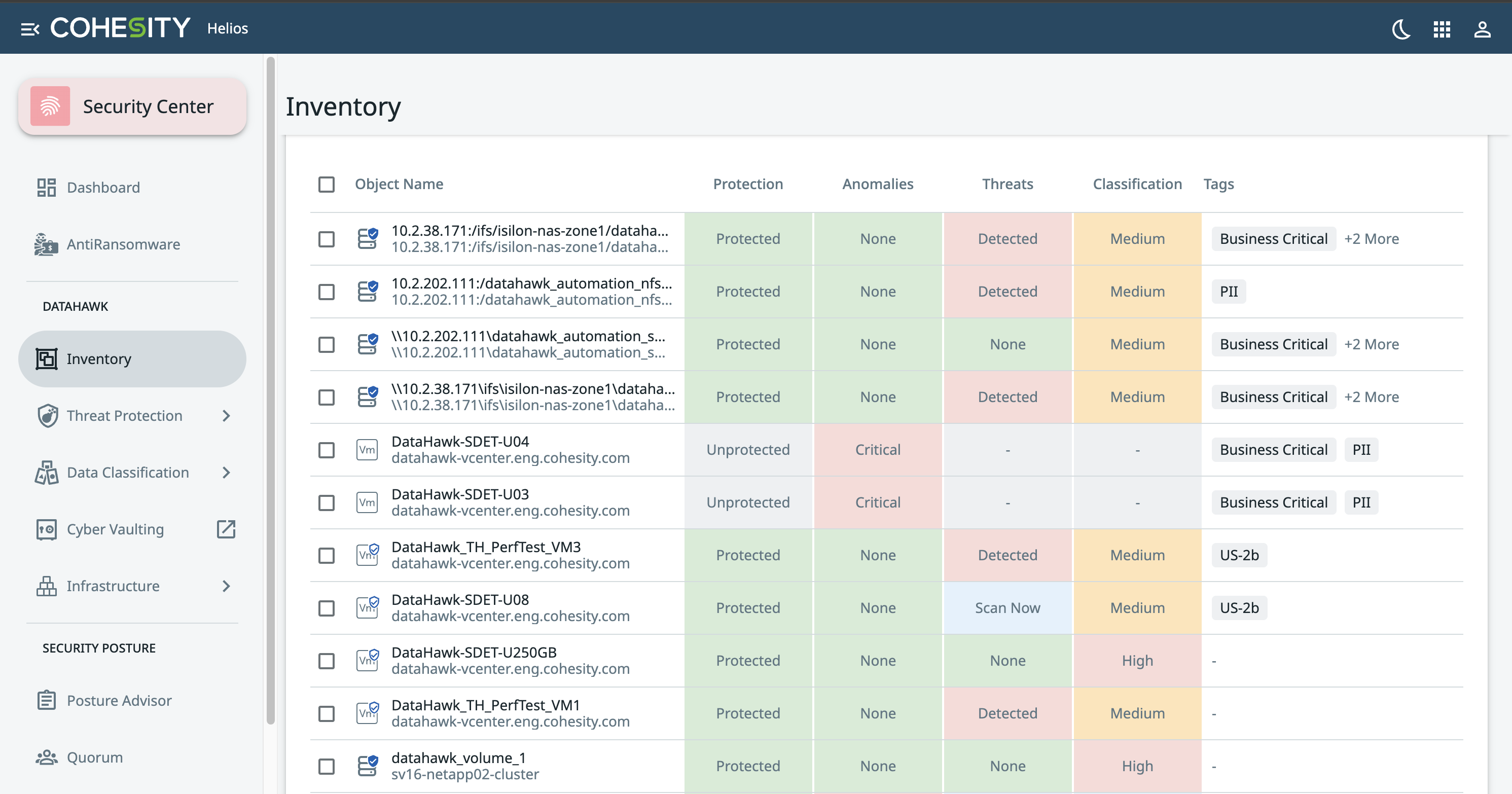
Improve security efficiency
Knowing that cyber resilience is a team effort, Cohesity established the Data Security Alliance with industry leaders like Cisco, BigID, Palo Alto Networks, Tenable, Microsoft, CrowdStrike, and Qualys. Together we collectively deliver critical technical integrations, best practices, and thought leadership to improve cyber resilience for the world’s largest organizations. Recently Cohesity announced the addition of six Data Security Posture Management (DSPM) security vendors to improve risk mitigation across enterprise data landscapes. We are excited to announce our first DSPM integration with Normalyze.
- Mitigate cyber recovery and compliance risk with Cohesity and Normalyze integration: This collaboration allows organizations to combine data classification capabilities from Normalyze with Cohesity DataHawk and enable rapid protection of sensitive and critical workloads across SaaS, PaaS, and IaaS environments. By combining insights about sensitive data discovered and classified by Normalyze with visibility into data backed up by Cohesity, you can rapidly identify and address data protection gaps. Enhance data security posture assessment, protect sensitive data as quickly as possible, and ensure compliance with incident reporting requirements in the event of a cyber incident.
In addition, Cohesity is thrilled to announce an integration with Zscaler to help organizations protect against double ransomware extortion. The new integration enables organizations to:
- Block exfiltration of sensitive data with Zscaler: By combining data classification for data-at-rest from Cohesity with data-in-motion protection from Zscaler, organizations can more effectively block exfiltration of sensitive data. Cohesity scans backup snapshots to discover sensitive data (e.g., PII). Zscaler leverages this information to fingerprint and index that data so that any suspicious transmission of that sensitive data is blocked, further protecting against ransomware-related exfiltration.
Ready to get started with your cyber resilience strategy? Download our eBook to learn about the key components needed to optimize data protection and minimize the impacts of a cyberattack.

















