Big announcements. Bold innovation.
See how to drive resilience everywhere: across AI, cloud, and identity.
Strengthen your cyber resilience
Respond faster and recover securely from destructive cyberattacks.

AI-powered data security and cyber resilience.
Cyberattacks continue to be the #1 threat to businesses.
These disruptive attacks result in lost revenue, excessive costs, fines, and reputational damage.
It’s time for a new approach.
Cohesity helps organizations like yours evolve their strategy, and adopt modern cyber resilience practices and technology. The end result: reduced risk, a stronger security posture, and a more resilient business.
Cyberattacks continue to be the #1 threat to businesses globally.
Threat actors are constantly innovating, and evading defenses.
of organizations were hit by ransomware attack in the last year.
lost for each hour of downtime
of successful breaches targeted exploits


The Cohesity 5 Steps of Cyber Resilience
Cyber resilience can be challenging. Here’s how Cohesity breaks down 5 steps to ensure your organization can bounce back quickly and confidently from cyberattacks.
Protect all data with global governance
Data sprawl is the silent killer – it's everywhere, fragmented, silos galore, increasing your attack surface. More data means more exposure, and more strain on your teams. But here's the win: Protect everything with a modern platform, and you reduce your risks from destructive cyberattacks.
Key actions:
- Deploy an API-driven data platform that handles 1000+ sources effortlessly: VMs, SaaS apps, databases, NAS, and so on.
- Ensure the platform spans on-prem, cloud, edge, SaaS – flexible deployment that follows your data as it grows over time.
- Centralize management tasks – use one pane of glass to rule them all, and spot risks before they compound.
Ensure your data is always recoverable
Cyber attackers often go after your backups first. Once they encrypt this data - you're cornered, forced to pay the ransom. Harden your platform with advanced security features– and you’ve taken big strides to improve your security posture. Add a cyber vault for additional protection.
Key actions:
Lock down access with multi-factor auth, role-based controls – zero trust all the way.
Make backups immutable – unchangeable, and able to be restored to production servers in case of ransomware attacks or data breaches
Deploy the cyber vault – logical air-gapping for ironclad isolation and an extra layer of resilience.
Detect and investigate threats
Cyberattacks are sneaky masters of deception, evading detection and often lying in wait to cause massive chaos. Unleash AI-powered threat detection, powered by cutting-edge threat feeds, with simple point-and-click threat hunting. Create custom YARA rules that help you identify advanced threats quickly, lowering risk.
Key actions:
- Be proactive by regularly scanning for threats in your backups. Practice good, consistent hygiene!
- Root out any changes as quickly as possible and identify malware or other vulnerabilities.
- Initiate threat hunting capabilities when seeking specific threats.
- Get your InfoSec and IT teams on the same page, using the same set of information with our security ecosystem integrations.

Practice application resilience
Congrats – with Steps 1-3 done, your platform's stood up, hardened, vaulted. You've scanned threats and hunted anomalies. Now? Practice your cyber resilience plan like a pro. Don't wing it during an actual attack: rehearse cyber response and recovery for infrastructure, data, and applications. Imagine: your systems down, pressure is mounting – but you're calm, because you've executed your plan plenty of times before.
Key actions:
- Orchestrate and rehearse: Automate processes, run drills to sequence response and recovery.
- Fire up the clean room: Conduct forensics to ID root causes and eradicate threats before you restore to production.
- Call in the experts: Lean on Cohesity CERT during attacks.
Optimize your data risk posture
Ransomware's evolving – nastier, sneakier. And your data? Exploding across on-prem, SaaS, cloud, edge. You're wondering, "What's lurking in that forgotten S3 bucket? Orphaned databases? Exposed creds?" Hidden dangers are everywhere.
But you can be proactive here: Data Security Posture Management (DSPM) flips the script and maps the right protection policies to data across your estate. If a breach does happen, you can use data classification to quickly identify your risks.
Key actions:
- Find out what data is where - scan your environments and assess what data is where and what protection level it has.
- Understand what may be in your backup estate and make sure it’s protected in the right way.
- Assess what may have been impacted in a breach or what may have happened in a case of data exfiltration.
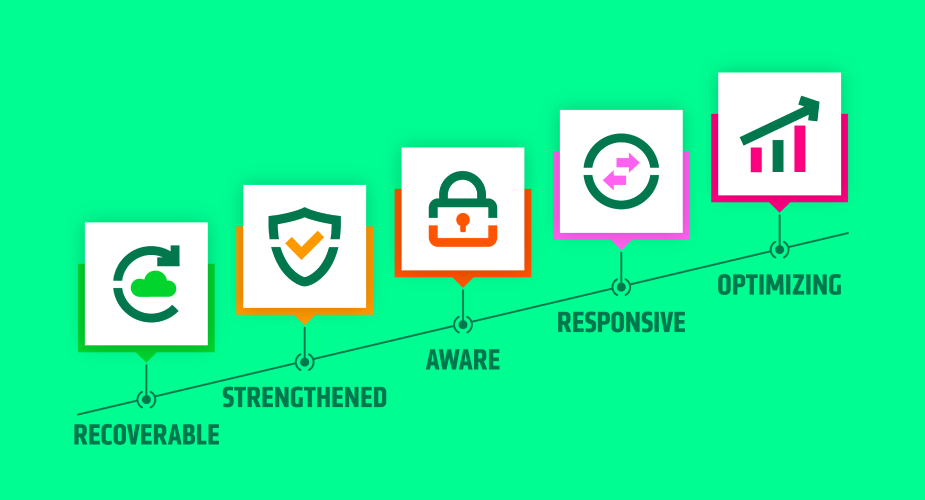
Introducing the Cohesity Destructive Cyberattack Resilience Maturity Model
Apply this model, based on popular cybersecurity response and recovery frameworks, to measure and improve your resilience.
Cohesity Data Cloud: What’s included
DataProtect
Simplify data protection, ensure recovery, and defend against ransomware with a modern, hyperscale solution.
Cohesity Gaia
Make smarter business decisions faster with AI-powered conversational search.
Threat protection
Protect and recover against ransomware. Find malware before it spreads using AI-powered threat detection.
SmartFiles
Take advantage of software-defined file and object services with next-level intelligence, scalability, and efficiency.
IT Analytics
Unified IT analytics and insights across multi-cloud environments now available as a cloud-delivered analytics platform.

See how you’d respond under pressure
Think you’re ready for a ransomware attack? Step into our hands-on, gamified simulator and put your incident response skills to the test.

Cohesity CERT (Cyber Event Response Team)
Minimized downtime and data loss: Expert incident response with robust recovery tools dramatically reduces the risk of data loss so your business can recover faster.
Rapid response to incidents: Cohesity CERT immediately steps in to help you contain the damage and initiate recovery.
Strategic partnerships: We’ve partnered with the world’s leading cybersecurity incident response firms, so you have what you need to respond to cyberattacks.
1Source: The State of Ransomware 2024 Sophos
2Source: The Hidden Costs of Downtime Splunk
3Source: M-Trends 2025 Special Report Mandiant

Ready to get started?
Start your 30-day free trial or view one of our demos.