Technology continues to evolve and so have the criminal actors behind ransomware attacks, which are among the biggest online security threats today. In recent years, ransomware attacks have increasingly become more sophisticated, focused, and expensive. It is estimated that “By 2019, global losses from ransomware attacks are expected to hit $11.5 billion”.
Criminal actors behind ransomware attacks now understand that legacy backup infrastructure is typically viewed as an insurance policy. These hackers have therefore started exploiting weaknesses associated with legacy backup, making it a prime target for attack. Several types of ransomware, such as Locky and Crypto, are known to destroy shadow copies and restore point data, making backup infrastructure easy prey for hackers rather than a defensive tool for enterprises.
It is not uncommon to see backup products touted for their ability to ‘detect’ a ransomware attack. However, these products fall short because they don’t have an efficient way to respond to a hack in a timely manner. In these cases, these legacy backup solutions lack:
- Integrated analytics allowing organizations to find which backups contain malware (prevents the malware from being restored along with the data).
- The ability to instantly recover at-scale.
Beyond Detection: Stopping Ransomware Attacks in its Tracks
Instead of relying on a legacy backup product that ransomware attackers prey upon, IT admins need to think about a comprehensive solution that will help prevent an attack on their backup infrastructure. The right solution will immediately detect a ransomware attack and alert IT admins who can respond quickly with corrective actions.
Cohesity is the only modern backup solution to offer a comprehensive, end-to-end solution against ransomware, and the only one that offers a multi-layer approach to prevent, detect, and – if the worst case happens – quickly respond to an attack, and ensure business continuity.
Let’s double-click on how the Cohesity Anti-Ransomware Solution is a complete solution.
- Prevent: Modern ransomware attack prevention requires a multi-layered defense approach and Cohesity offers that with the combination of:
- Immutable File System: At its core, Cohesity’s immutable file system, SpanFS, keeps the backup jobs in time-base immutable snapshots. The original backup job is kept in an immutable state and is never made accessible, which prevents it from being mounted by an external system. The only way to mount the backup in read-write mode is to clone that original backup, which is done automatically by the system. Although ransomware may be able to delete files in the mounted (read-write) backup, it cannot affect the immutable snapshot.
- DataLock: DataLock is a WORM-like capability that offers another layer of protection against a ransomware attack. This capability enables security officers to create and apply a “Datalock” policy to selected jobs and achieve a higher order of immutability for protected data – something that security officers – and admins – cannot modify/delete. This feature integrates with RBAC, eliminating the need for third-party tools.
- Multi-factor Authentication: As much as we want passwords to offer guaranteed protection, passwords get compromised all the time. Cohesity offers multi-factor authentication, which is the best way to mitigate against phishing schemes and other password hacks.
- Detect: In a perfect world we won’t need to worry about a lot of things, including ransomware, but bad things do happen. In a situation where your primary environment, your users, and application infrastructure is compromised, Cohesity Helios can help you out of that jam. With its latest anomaly detection, Helios, our SaaS-based machine-drive solution, will provide eyes and visibility when you’re not able to. With SmartAssist, Helios will alert not just the IT admin but also Cohesity’s support team when the primary files data-change rate is out of the norm. Anomalies will be detected based on matching any larger data changes against the normal patterns, including:
- Daily change rate on logical data.
- Daily change rate on stored data (post-dedupe).
- Pattern-based on historical data ingest.
Besides monitoring the backup data change rate to detect a potential ransomware attack, Cohesity very uniquely detects and alerts for file-level anomalies within unstructured files and object data. This includes analyzing the frequency of files accessed as well as the number of files being modified, added, or deleted by a specific user or an application in order to ensure a ransomware attack is quickly detected.
- Respond: The most important requirement after a ransomware attack is having the ability to quickly recover compromised data. Unlike any solution available in the industry today, Cohesity offers the ability to locate and delete infected files across your global data footprint, including in the public cloud. Your apps and data are instantly brought back using Cohesity’s instant mass restore by offering:
- Unlimited Scalability: A web-scale platform that allows IT admins to grow their Cohesity cluster from three to unlimited nodes with the ability to store unlimited snaps and clones without any performance impact.
- Global Actionable Search: Unique, Google-like global search capability that allows you to quickly locate data and infected files and take appropriate corrective actions. This includes finding a malicious file across all workloads – and – taking necessary action to contain it.
- Instant Mass Restore: When ransomware strikes, you are not dealing with one, two, or a few VMs/files, but rather a disaster recovery scenario in which the IT admin needs to recover hundreds of VMs. Unlike other backup solutions, traditional or modern alike, it can take days, if not weeks to recover. With Cohesity’s instant mass restore, IT admins can recover hundreds of VMs instantly, at scale, to any point in time. Here are additional details:
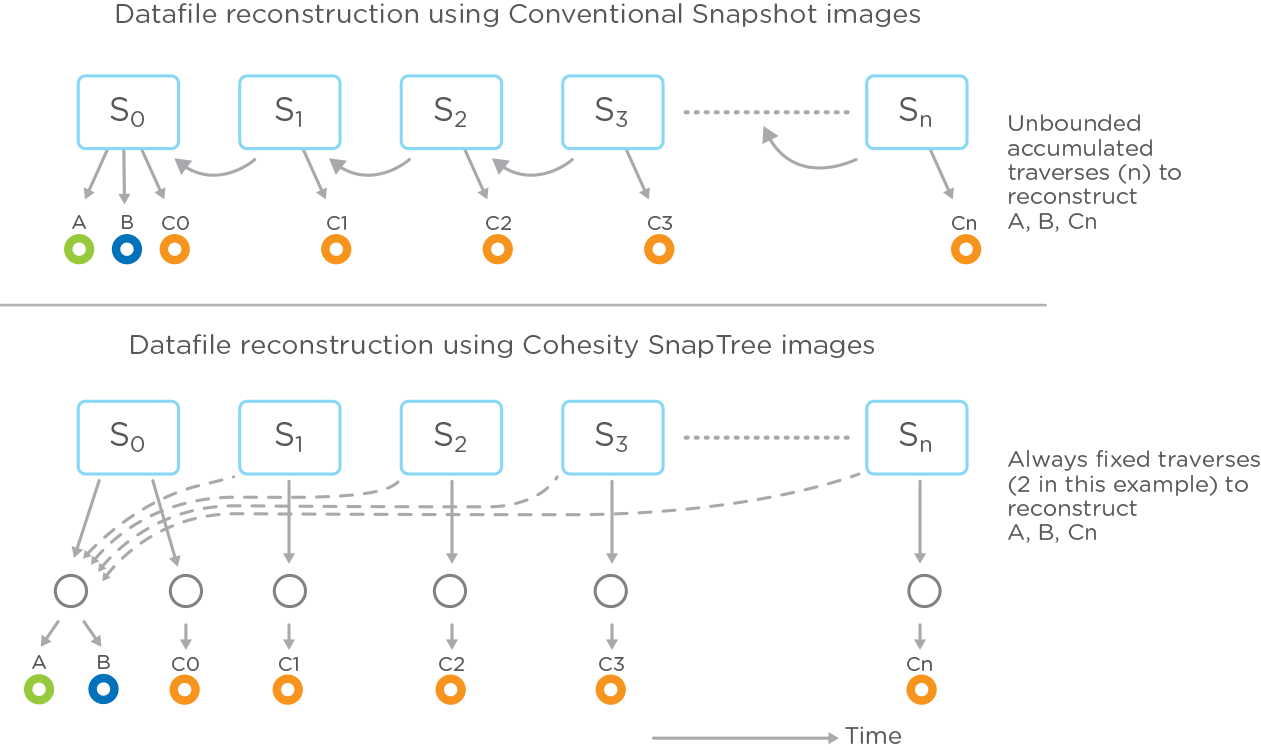
- Cohesity’s patented B+ tree metadata structure keeps any recovery no more than two hops away.
- All snapshots on Cohesity are kept fully hydrated (i.e. in the same format as in the original VM environment), so the system doesn’t have to spend time and resources in stitching backups.
- Because SpanFS is a distributed file system that mounts the data using NFS/SMB protocols, data is instantly available while the recovery is happening in the background.
Ransomware is so common it has practically become a household name. Yet ransomware remains a daunting threat to enterprises in need of a modern solution that offers more than the ability to simply detect a threat. Below are a few helpful links to learn how Cohesity offers a comprehensive solution against ransomware attacks.