A Changing Data Landscape
You’ve heard it before: exponential data growth, more clouds, more end-points, and a shift in the way we work and access data remotely. These are all key elements of our data landscape that can’t be ignored, and they make the challenge of managing data, whether for protection such as backup or recovery, or governance more challenging. That said, backups have always had their place as your last line of defense insurance policy if something goes wrong and you need to recover data. Data governance on the other hand helps you be proactive about your data: where it is, who has access, how long you should keep it so your organization can maintain internal controls or stay ahead of legal, regulatory, or compliance mandates to avoid fines and penalties. Two useful but separate functions that up until now operated independently.
Ransomware Changes the Game
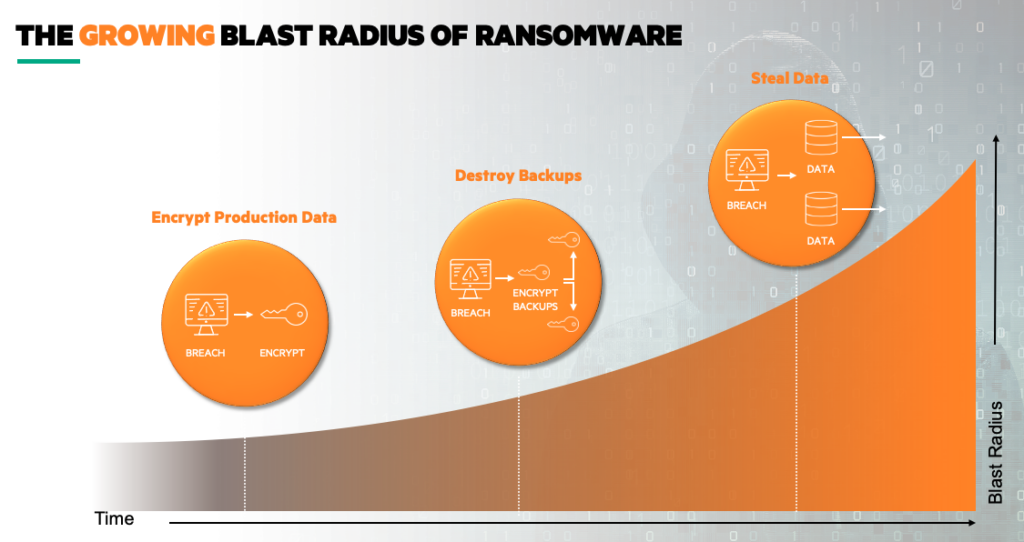
The sophistication and blast radius of ransomware attacks has grown in the past few years. This evolution has to change the way you look at managing, protecting, and governing your data. Let’s examine the diagram below in more detail.
Ransomware 1.0 — Encrypt Production Data
When ransomware first appeared, its primary target was your production data — encrypting it so cybercriminals could bring your business operations to its knees. And the way out of your problem? If you paid their handsome ransom, they would provide you with keys to unlock and decrypt your data so you get back to business. This worked on consumers or small businesses, but enterprises and well-run organizations literally had a backup plan.
Ransomware 2.0 — Destroy Backups
So ransomware got more sophisticated — they went after your insurance policy by lurking for weeks or even months systematically encrypting or destroying your backups before launching a full-scale attack on production. Why? With both your production and backup data compromised, you’ll likely have no choice but to pay the ransom. Enterprises that were better prepared than others fought back and protected their backup data as well using a modern solution like Cohesity that provides data immutability to protect it from tampering or destruction.
Ransomware 3.0 — Steal Data
In an on-going arms race, ransomware has recently taken another turn for the worse. Cybercriminals realized that once they’ve gotten access to your systems through malware, phishing, or other means — not only can they encrypt your data, but they can steal it as well. This is called ransomware double extortion where cybercriminals can extort a ransom payment for decrypting your production data and not leaking your stolen data to the public or dark web. This double extortion tactic works so well that according to Coveware over 83.3% of ransomware attacks in Q3 2021 included data theft and exfiltration.
With cybercriminals changing the rules and playing dirty, backup and IT leaders need to change the way they manage their data. Just having a robust backup and recovery strategy may not be enough to keep ransomware at bay.
Rethinking the Role of Data Governance
The passing thought of data governance might have you thinking about lawyers or compliance officers — not folks you normally work with. That may be true, but it ought to change. Why? Because not all data is created equal. For backup, you want to back up most if not all of your useful data. That can be John’s marketing photos, Symona’s sales presentation, or Li Ping’s customer spreadsheet with personally identifiable information (PII). But to cybercriminals and your business, the customer data is much more important and sensitive if it was to be stolen and leaked out.
Classifying Data
So the first step in managing risk for your sensitive data is to understand what data you have, where it is, who has access, and if that data is important or sensitive. Frankly, with continual growth of data volumes and the locations and devices in which data is stored, finding and classifying your sensitive data is like looking for a needle in the haystack.
Traditional Data Governance Tools
Data governance and the broad range of tools and use cases it addresses deserves much more coverage than just this blog post. Using the DAMA data management body of knowledge as reference, there are nine domains that encompass data governance. Data quality and master data management may be ones you’ve heard about, whereas others such as metadata may be lesser known. A newer area of data governance that you should care about is automated enterprise discovery and classification of structured data, unstructured data, or both. That said, they’re not necessarily designed for backup or data security in mind — they might be good at classifying information and flagging data that might be out of compliance or not meeting business rules, but how can they help during a ransomware attack?
Backup and Data Governance
The idea of backup data reuse has been around for some time, whether it be for development/test or analytics. A relatively new idea is to reuse backup data to help with data governance. Backups already capture a broad set of an organization’s data — why not reuse it to classify data and discover sensitive information? This is a less disruptive way of scanning and classifying information as it doesn’t require tapping into production systems and can be offloaded to the backup solution if it is capable of doing so. Once you’ve classified data, you have a better idea of where your sensitive or regulated data is which is helpful, but how do you determine which sets of sensitive data might be at a high risk of an attack or breach?
Intersection of Data Backup, Governance, and Security
“Call security!” – says Captain Obvious. Combatting the breadth and frequency of ransomware attacks requires a village —ransomware can’t be neutralized with just one tool or one team. As a backup or infrastructure practitioner, your organization will lean on you if and when a ransomware attack occurs and your job will be to ensure your backup data is clean and able to recover your production systems as quickly as possible. That addresses ransomware 1.0 and 2.0 scenarios, but what about 3.0 style attacks that include data exfiltration?
You can help your data governance and security colleagues with backup data and reusing it for data discovery and classification. But classifying sensitive data is only part of the equation. What if you had a solution that could help you detect data overexposure and inappropriate access, sharing, and downloads? That can help your security team address a potential ransomware attack in progress.
Cohesity Brings It All Together
Cohesity’s next-gen data management solutions and Threat Defense data security architecture helps bring together all the key elements of data backup and recovery, data governance, and data security required for you to combat all types of ransomware. Cohesity DataProtect helps you rapidly recover your production systems from ransomware 1.0 attacks and uses immutability to protect your backup data from tampering or deletion used in 2.0 attacks. Coming soon, Cohesity FortKnox will provide an additional layer of security by isolating a second or third copy of production data within a Cohesity-managed vault or “virtual air gap.” The vault data is designed to be tamper-resistant within an operationally independent environment and is always available in case of a ransomware attack or disaster.
In early access preview, Cohesity DataGovern will bring together key elements of data governance and security while tapping into our core backup capabilities to help combat ransomware 3.0 double extortion and data exfiltration. It will efficiently help you classify information and discover the sensitive data without impacting your production systems. It will be designed to enhance data security, by scanning production data using machine learning (ML) based anomaly detection and user entity behavior analytics (UEBA) to detect overexposure or anomalous activity involving your sensitive data such as inappropriate access, sharing, and unusually high file activity in near real-time that might be an early indicator of a ransomware attack. Integration with leading security orchestration automation response (SOAR) tools will help your security team respond and remediate quickly to a situation before it escalates to a full scale attack or large scale theft.
Be the Hero in the War Against Ransomware
“War brings out the worst and the best in people.” ~ Major Dick Winters, decorated US Army veteran
IT organizations across the globe are no doubt at war with cybercriminals and ransomware. Now is your time to shine and bring the people together from data backup, governance, and security and implement the right solutions to win against ransomware. You can start with Cohesity. Sign-up today for a 30 day free trial for DataProtect delivered as a Service and start backing up your valuable data in minutes.
Learn more about DataGovern and how it helps classify sensitive data and detect anomalies as well as Cohesity FortKnox for data isolation.